SOC 2® Compliance Builds Trust
Relying on trusted third-party service organizations to perform ongoing specialized skills, tasks, functions, and projects is an extremely attractive strategy for businesses of all sizes and industries today. To provide assurance regarding internal controls, it is important that service organizations undergo assessment and attestation, such as a SOC 2 audit.
SOC 2 audits review controls related to the AICPA’s Trust Services Criteria. A SOC 2 report on internal controls demonstrates an organization’s commitment to security, availability, processing integrity, confidentiality, and privacy.
ADVANTAGES
Why Pursue SOC 2 Compliance?
SOC 2 audits foster customer trust, which can lead to sales growth. They represent a competitive advantage by showing adherence to best practices, while proactively addressing risks and identifying potential vulnerabilities. Being SOC 2 compliant reduces the risk of fines and penalties tied to regulatory non-compliance. Plus, the SOC 2 audit process improves security posture by evaluating current policies, processes, and controls, strengthening defenses against cyber threats.
WHAT’S INCLUDED
SOC 2 Audit Services
The I.S. Partners, LLC. SOC 2 auditors regularly work with users and service organizations to help both parties achieve top-level compliance for a secure business relationship that benefits everyone involved. We provide two types of SOC 2 audit services:
SOC 2 Type I Audit
This audit focuses on the service organization’s controls used to address any or all five Trust Service Criteria, providing assurance of effective design at a specific point in time.
SOC 2 Type II Audit
This audit type adds attestation that the service organization’s controls are tested for operating effectiveness over a period of time, typically six months.
What our SOC 2 Audit Services Deliver
SOC 2 compliance is essential for businesses that aim to build trust with their clients and demonstrate their commitment to secure, confidential, and reliable services. I.S. Partners offers expert SOC 2 audit services, guiding your organization through the audit process to ensure compliance and achieve a competitive edge. Utilizing our extensive experience and knowledge, we help businesses worldwide in improving their cybersecurity posture and adhere to the AICPA Trust Services Criteria.
What a SOC 2 Audit Covers
PROCESS
SOC 2 Preparation & Audit Success
SOC 2 Preparation & Audit Process
This audit focuses on the service organization’s controls used to address any or all five Trust Service Criteria, providing assurance of effective design at a specific point in time.
- Determine the scope: Company level or specific service
- Select desired Trust Services Criteria (TSC) based on your company, industry, and requirements
- Identify relevant information security controls and systems
- Gather necessary documentation (e.g., asset inventories, policies, and response plans)
SOC 2 Self-Assessment
Some organizations opt for an internal SOC 2 self-assessment to identify gaps and create a remediation plan before the formal SOC 2 audit. The self-assessment process involves four key steps:
- Define the audit scope
- Map compliance requirements against the TSC and Common Criteria
- Create a priority list for evidence collection
- Develop a remediation plan for each identified gap
- Share self-assessment outcomes, gap findings, and remediation plans with relevant stakeholders
Readiness Testing
Readiness assessments for SOC engagements are valuable fact-finding tools when approaching a SOC 2 audit. They are most useful when conducted by an external, CPA consultant.
- Conduct a pre-assessment to evaluate control environments
- Focus on necessary processes and systems for the audit
- Identify areas for improvement
Close the Gaps
Using the information from the self-assessment and/or the third
- Compare your current controls and systems with SOC 2 requirements
- Develop remediation strategies before the official audit
- Implement the remediation plan
- Follow-up to assess progress made
SOC 2 Audit Process
- Auditor collaboration: Initial contact, scheduling, and communication
- Auditor collaboration: Initial contact, scheduling, and communication
- Gathering evidence of controls: Provide auditors with required documentation
- Evaluation: Walk through business processes and security practices with auditors
- Follow up: Respond to additional evidence requests, clarifications, and gap remediation
- Completed SOC 2 Report: Obtain a written report, address exceptions, and celebrate if successful
Audit Frequency
SOC 2 Type II audits are typically conducted annually, but in certain situations, you may opt to perform them twice a year. Moreover, it is not uncommon to undertake a SOC 2 Type II audit a few months after completing a SOC 2 Type I to ensure continued compliance.
AUTOMATION
Get the Best SOC 2 Compliance Software for FREE
Introducing automated SOC 2 audit software, by Fieldguide, designed to simplify and streamline audit engagements from evidence collection to reporting. With a collaborative cloud platform, automated workflows, and comprehensive reporting, our software ensures a stress-free SOC 2 audit experience.
Key features include a compliance dashboard for progress monitoring, real-time team collaboration, framework templates for audit preparation, and efficient document collection. This SOC 2 software offers an end-to-end compliance and risk management system, led by our knowledgeable CPAs and SOC 2 auditors, blending technology and expertise for an optimized risk and compliance program.
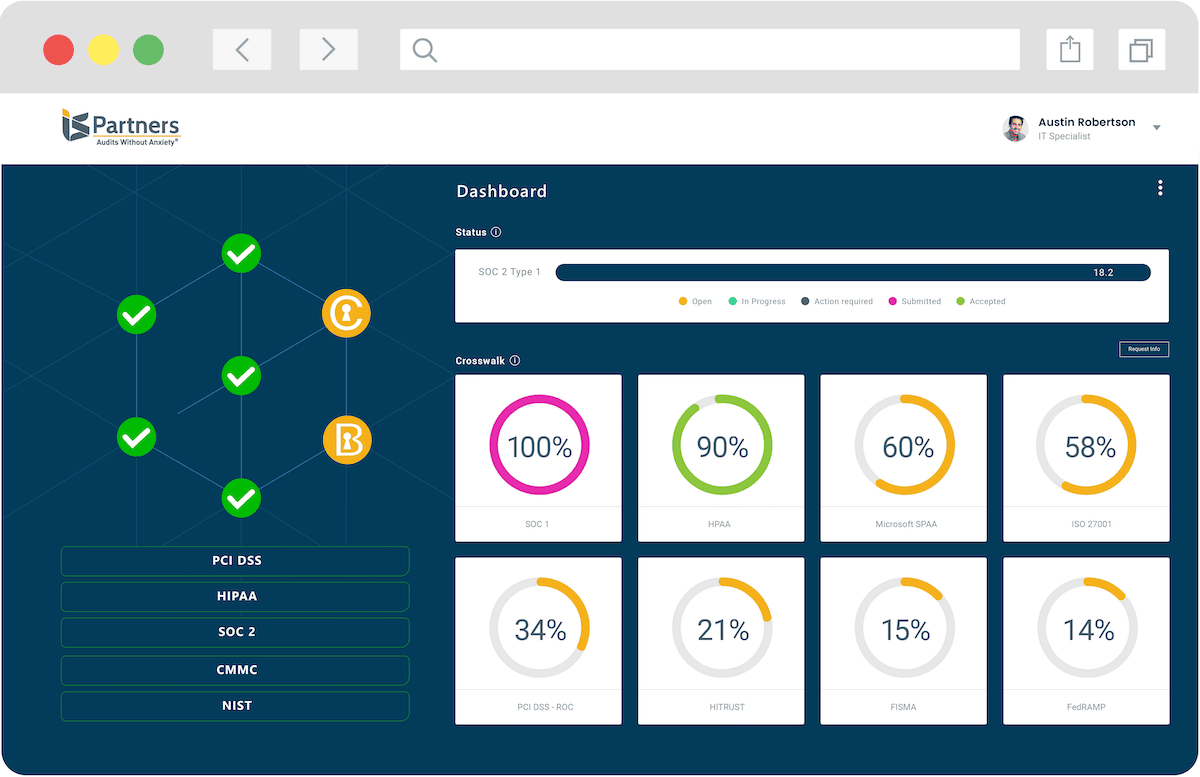
Free SOC 2 Audit Software for Our Clients
Fieldguide automated SOC 2 audit software is free to use for all I.S. Partners clients. Start working with us and getting faster, less expensive compliance engagements.
VALUE
How to Choose the Best SOC 2 Auditor?
We are a licensed CPA firm and member of the AICPA & CIMA, specializing in SOC 2 compliance. The practitioners at I.S. Partners have over 20 years of experience providing successful SOC 2 audits for businesses worldwide. Additionally, our in-house, U.S.-based team of experienced SOC 2 auditors with a deep understanding of requirements.
GET STARTED
Your Trusted SOC 2 Audit Firm
Ready to start your journey towards SOC 2 compliance? Simplify the process by partnering with I.S. Partners, a trusted provider of SOC 2 audit services. Fill out our online form for more information or to request a quote for SOC 2 audit services tailored to your organization’s needs.
FAQs





