Just Released: New Version of PCI DSS
With the release of PCI 4.0, the clock has started ticking for companies that transmit and use payment card information from consumers to transition to the new framework. With the compliance deadline less than two years off, the time to assess readiness and close the gaps is NOW.
The Payment Card Industry Data Security Standard (PCI DSS) continues to provide the most comprehensive information security standards. This is because the PCI Security Standards Council is continually looking at the way the industry operates and looking for ways to improve it. Specifically, it is concerned with enhancing the way businesses handle such things as the development, storage, dissemination, and security for data. As such, it occasionally issues new updates for businesses to improve their practice in these areas and ensure compliance.
Towards a Zero Trust Approach
Although a ‘zero trust’ model is not directly mentioned in the new standard, the PCI Security Standards Council is moving in that direction. Looking at how the standards are different in PCI 4.0, we see a trend. There is a subtle shift from precise technical specifications to a broader view of security.
The PCI DSS 4.0 standard was developed with a zero-trust philosophy, allowing firms to create their own distinctive, pluggable authentication systems to satisfy the legal requirements for data protection. Another example is that the new version de-specifies components like software security, in favor of component-level design. PCI 4.0 also features crucial upgrades regarding user and system access authorization and authentication across an environment. Effective IAM and MFA combined with encryption is the overarching principle behind zero-trust security for protecting sensitive cardholder data and safeguarding online payments.
This shift towards a ‘zero trust’ model makes sense. As we look beyond this most recent version of PCI DSS and toward the future, this is the direction that the entire cybersecurity industry is currently moving.
PCI 4.0 Compliance Date: March 31, 2025
The PCI SSC released version 4.0 at the end of March 2022, although PCI DSS v3.2.1 will remain active for two years through March 2024. The period of transition to when PCI 4.0 goes into full vigor in March 2025 is already underway!
Prepare for PCI 4.0
PCI 4.0 Transition Timeline
This transition period, from 2022 to 2024, gives organizations time to become familiar with the new version, update their reporting systems, and plan for and implement changes to comply with the updated requirements. Training for QSAs and ISAs to perform PCI 4.0 assessments was held in mid-2022. Now, PCI audit practitioners are working with organizations to develop a plan for compliance transitioning.
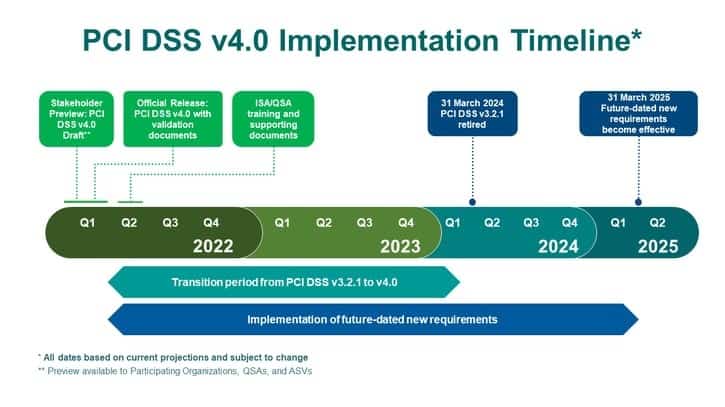
Timeline provided by the PCI SSC.
In preparation for PCI 4.0 going into effect, we recommend that organizations plan for budgetary changes to adapt to the new requirements and additional risk-based security testing. Implementing more significant changes will demand staffing and training efforts as well.
What Changes Does PCI 4.0 Introduce?
Because many of the PCI security controls are 10 years old and major changes haven’t been made since 2015, so PCI DSS 4.0 is significant.
Six specific areas are affected by credit card data security standards. These areas are focused on security, customized implementation, authentication, encryption, monitoring, and critical control testing frequency methods.
6 Key Changes Introduced by PCI 4.0
Here’s a closer look at the main PCI DSS 4.0 changes that companies will notice as they transition to the new standards:
1. Flexibility: Customized Implementation to Meet the Intent of Security Controls
This is probably the biggest change that will be ushered in with the release of PCI 4.0. The 12 requirements will be shifted to focus on the main security objectives:
- Ensure the standard continues to meet the security needs of the payments industry,
- Add flexibility and support of additional methodologies to achieve security,
- Promote security as a continuous process,
- Enhance validation methods and procedures.
The new, customized validation approach will sharply define the security outcomes linked to each requirement. With PCI DSS 4.0, organizations will then be able to choose to perform the control as prescribed or opt for customized implementation. With customized implementation, companies can comply by showing that the intent of the requirement is met without needing to provide an operational or technical justification.
Similar to compensating controls, this change will allow businesses more flexibility in modifying implementation procedures and meeting requirement intent. To verify the effectiveness, external assessors must review the documentation and thoroughly test each control with a custom implementation.
2. Security: More Stringent Requirements
The ultimate goal of PCI DSS is still to ensure that all sellers safely and securely store, process, and transmit cardholder data. To that end, PCI 4.0 sets the bar higher and builds on the assurance of PCI-DSS v3.2.1. In addition to restructuring many requirements, the Summary of Changes includes stronger security standards. Top management, including CISOs and CTOs, should prepare to adjust budgets to allocate capital and operational funds to implement the new requirements.
3. Authentication: Deeper Focus on NIST MFA/Password Guidance
NIST/Password Guidance moves to the forefront in this new version. The PCI SSC places more focus on applying stronger authentication standards to payment and control process access log-ins. It has also partnered with Europay, Mastercard, and Visa (EMVco) to implement the use of a 3DS Core Security Standard during transaction authorization.
This new standard opens the door for organizations to build their unique pluggable authentication standards to meet data security regulatory requirements. At the same time, they can be scaled to fit the company’s transaction objectives.
4. Encryption: Broader Applicability on Trusted Networks
The push for more secure standards related to cardholder data security has increased. Cyber threats that include malicious code is one of the biggest problems that financial institutions face. Once the code is embedded in the network, information can be retrieved through cardholder data being transmitted. The new version of PCI 4.0 specifically addresses this issue, with best practices and insight on how to fully protect network transmissions.
5. Monitoring: Technology Advancement Requirements
There are more risk-based approaches in the new PCI DSS 4.0. Technology is growing rapidly, and companies are looking at pluggable options for their information systems, much like the PCI Software Security Framework. The adoption of these solutions allows organizations to comply with standards while gaining faster deployment of processes without having the technology located in a specific control area.
6. Critical Control Testing Frequency: Possible Inclusion of DESV Requirements
This is a higher level of critical control testing, which includes a significant increase in the amount of testing required. Though Designated Entities Supplemental Validation (DESV) requirements are nothing new, they were previously mandatory only for companies that had been compromised.
Related article: How to Keep Employees and Your Organization PCI Compliant.
Prepare for PCI 4.0
Other Recent Updates from the PCI SSC
Since 2015, SSL/early TLS encryption protocols were deemed as no longer secure, according to Jones Day. At that time, the Payment Card Industry Data Security Standard (PCI DSS) offered important guidance about the vulnerabilities within the Secure Sockets Layer (SSL) protocol, as well as problems with early versions of the Transport Layer Security (TLS) protocol.
The PCI Security Standards Council (SSC) originally ordered the removal of SSL and early TLS versions from cardholder data environments by June 2018. This required companies to disable SSL/early TLS encryption tools to adopt and implement a more secure encryption protocol. At that point, the PCI SSC strongly suggested the implementation of TLS v1.2 for peak protection.
Start the Transition with a PCI Readiness Assessment
Handling and transmitting cardholder data, as well as performing transactions, needs to be performed in a secure information security environment with the correct controls in place to minimize risks. Learn whether your systems are PCI DSS 4.0 compliant with specialized testing from I.S. Partners.
We make the process easier by offering a range of assessments and advisory services tailored to your business framework. With a PCI DSS Assessment, you can minimize risks, identify security vulnerabilities, and further protect cardholder data from breaches.




