Key Takeaways
1. A HITRUST compliance checklist helps organizations keep the compliance process organized.
2. HITRUST requirements are organized into 19 domains with 135 controls, each tailored to an organization’s size, risk, and operational needs. However, not all organizations need to implement every control.
3. At IS Partners, our certified assessors identify security gaps and assist in applying controls to achieve critical maturity levels for HITRUST certification.
What Is a HITRUST Compliance Checklist?
A HITRUST compliance checklist is a guide that helps organizations identify, implement, and verify the controls necessary for aligning with the HITRUST Common Security Framework (CSF).
A checklist helps organizations focus on the security governance controls that are most relevant to their needs to fast-track the HITRUST certification process.
1. Assess and Define Scope
Begin by identifying all systems, processes, and personnel that process or interact with sensitive data. This includes understanding your organization’s business functions, technology stack, and data flow to determine what falls under the scope of HITRUST.
A well-defined scope helps minimize audit costs and ensures focus on the most critical areas for compliance. IS Partners’ Director for Healthcare Compliance weighs in on how our team ensures a unique and effective approach for HITRUST compliance,
Most organizations tend to over-scope the engagement. This causes the assessment to be overwhelming for those performing HITRUST assessments for the first time. To alleviate that, we introduce all first time assessments by performing a HITRUST workshop. The workshop was developed from our 10 years of experience to provide the fundamental basics of the assessment so that there is a sense of comfort.
During the workshop, we will detail what to expect during the HITRUST assessment. This ranges from how to assess the scope of the assessment, scoring of the assessment, interaction with us as assessors and what to expect during QA.
2. Understand HITRUST Requirements
Familiarize yourself with the HITRUST CSF, which integrates regulations such as HIPAA, NIST, ISO, and GDPR into a unified framework.
This allows organizations to manage multiple compliance mandates simultaneously. Study the various maturity levels in the HITRUST framework, as they measure your organization’s security practices and policies.
3. Engage an External Auditor
Early collaboration with a HITRUST-approved external assessor ensures you align your readiness efforts with certification expectations. These auditors bring expertise in identifying compliance gaps and offering actionable recommendations.
Working with them from the beginning reduces the likelihood of delays or expensive remediation during the certification phase. LaRocca emphasizes the impact of having an expert external auditor, highlighting how their guidance significantly enhances efficiency,
When engaging with us we understand that your organization has daily operations besides completing the HITRUST assessment. Therefore, we work with you to best achieve certification while working within the confines of your operations.
To achieve that, we engage with you we will discuss options on how to structure the engagement. While we have our own project management platform that you can access, we also work within many different internal audit, GRC and document repository applications.
4. Conduct a Readiness Assessment
Perform a gap analysis to compare your current security controls against HITRUST requirements.
This assessment will identify strengths and weaknesses, helping you prioritize remediation efforts.
Whether done internally or with an external partner, readiness assessments provide a roadmap to compliance.
5. Develop Corrective Activities
Address identified gaps by creating specific, measurable remediation plans using tools like MyCSF. Corrective actions might include updating outdated policies, patching systems, or implementing new security technologies.
Tracking progress ensures that all identified deficiencies are resolved before formal assessment begins.
6. Develop Policies and Procedures
Document comprehensive policies covering areas such as risk management, incident response, access control, and data protection. Policies should be easy to understand and actionable for employees.
Effective documentation also supports organizational accountability and ensures the long-term sustainability of compliance efforts.
7. Implement Security Controls
Deploy the necessary technical, administrative, and physical safeguards outlined by HITRUST CSF. Examples include multi-factor authentication, vulnerability scanning, and intrusion detection systems. Embedding these controls into day-to-day processes ensures they become a natural part of business operations.
8. Protect Sensitive Data
Use robust encryption methods, such as AES-256, to protect sensitive data both at rest and in transit. Implement strong access control measures, ensuring that only authorized personnel can view or handle protected data.
Secure file transfer protocols and data loss prevention tools can further enhance data security.
9. Conduct a Validated Assessment
Engage a third-party assessor to perform an independent review of your implemented controls and processes. This assessment typically includes interviews, documentation review, and testing of controls.
A thorough, validated assessment increases the likelihood of achieving certification on the first attempt.
10. Submit for HITRUST Review
Once the third-party validated assessment is complete, submit the results to HITRUST for quality assurance and certification review.
The HITRUST Alliance evaluates the findings, ensuring they meet the framework’s stringent standards. Timely submission and accurate documentation improve the speed of certification issuance.
11. Certification Awarded
Upon successful review, HITRUST issues certification, signifying your organization’s adherence to industry best practices. Certification demonstrates your commitment to data protection, boosting customer trust and market competitiveness. Many organizations also leverage this certification as a selling point for their services.
12. Ongoing Monitoring and Maintenance
Maintaining compliance is an ongoing effort that requires regular evaluation of your security controls. Conduct periodic internal audits, update policies in response to evolving threats, and ensure employee training stays current.
HITRUST certification must be renewed every two years, but continuous monitoring simplifies the re-certification process.
Why Use a HITRUST Compliance Checklist?
Ensuring HITRUST compliance can be a complex process, but a structured approach simplifies it. A HITRUST compliance checklist provides a clear roadmap for organizations, helping them track progress, mitigate risks, and improve readiness for certification.
By systematically addressing each requirement, businesses can enhance security, avoid regulatory pitfalls, and streamline their path to HITRUST CSF certification. Specifically, this checklist can help you perform the following tasks:
- Track progress. It enables organizations to monitor what has been completed and what remains to be done. This provides a clear snapshot of your compliance status according to the HITRUST standards at any given time.
- Reduce risks. A checklist helps companies reduce the risk of overlooking HITRUST CSF certification requirements. Overlooking requirements creates security vulnerabilities and leads to regulatory penalties.
- Improve readiness. Since there’s a clear record of completed actions, a checklist helps organizations better assess their audit and certification readiness.
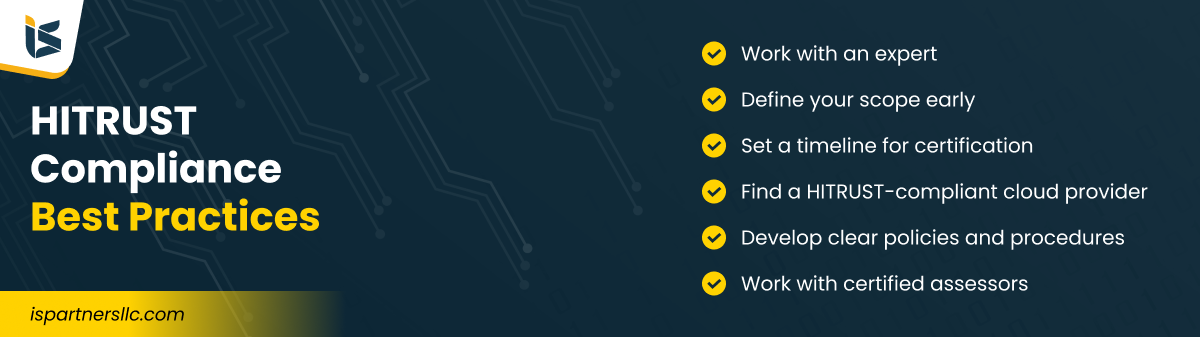
HITRUST Compliance Best Practices
The most important best practice for HITRUST compliance is to work with an expert. The HITRUST CSF is complex and requires expert assistance for correct implementation. Here are some more considerations:
1. Define Your Scope Early
Before you begin making changes to your systems, understand what the HITRUST certification requires. This includes going through the 19 domains, 14 control requirements, and certification scoring methods.
Once you know what you need to implement, identify the systems, processes, and data that fall under HITRUST requirements. A risk assessment will help you find assets that need to be protected, data that’s collected, where data is stored, and who has access to it.
2. Set a Timeline for the Certification
No matter which level of HITRUST certification you go for, you’ll need to plan and implement a solid security plan. This takes consistency and time. To make sure everything goes correctly, you should:
- Note down key milestones (such as completing readiness assessments)
- Plan how to implement controls
- Learn how to submit for validation
This will help you develop a clear framework that will enable you to address any gaps identified along the way.
3. Find a HITRUST-Compliant Cloud Provider
Your system’s infrastructure helps you provide services and keep data safe. If you’re storing sensitive information on the cloud, find a cloud provider that is HITRUST-compliant—like Amazon AWS—to manage access and incident responses.
You should make sure your provider has:
- Solutions that support your specific compliance needs
- The capability to protect your system
- Defined protocols for detecting, responding to, and recovering from data security incidents
4. Develop Clear Policies and Procedures
HITRUST compliance requires your organization to have SOPs for recurrent or daily operations. These need to be replicable and should create evidence (that can be used to certify) in the form of access logs, data requests, and processing times.
You should establish procedures and policies around:
- Access control—Define the roles and responsibilities for granting, revoking, and reviewing access to sensitive systems. You should also specify steps for procedures as well.
- Incident management—You should require prompt reporting of security incidents and outline exactly how to identify, log, escalate, and resolve incidents.
- Business continuity and disaster recovery—Establish policies that help maintain operations during disruptions in the form of a step-by-step guide.
5. Work With Certified Assessors
HITRUST CSF requirements and controls are complex and detailed. As a result, many organizations find it difficult to understand what level they apply to. The maturity score and the rubric also make it harder to understand how to implement policies that ensure certification.
That’s where a certified assessor comes in. A HITRUST external assessor at IS Partners would simplify the compliance process for you and help you identify gaps in your system.
Your assessor will also help you evaluate whether your organization’s controls are appropriately scoped to its environment (e.g., cloud-based systems, remote access, or sensitive data classifications) and provide advice that would help you work on weaker areas.
Is HITRUST Compliance Mandatory for Healthcare Organizations?
No. HITRUST compliance is not legally mandatory for healthcare organizations. However, a HITRUST r2 assessment and certification is considered a gold standard in risk management and compliance assurance for organizations across all industries.
In fact, a proper r2 assessment can provide coverage for 60 frameworks and standards, including:
- Federal and internal legislation—HIPAA, GDPR, DORA, etc.
- Regulatory agency rules and standards—NIST SP 800-53, FTC, CMS, etc.
- State legislation—California Consumer Privacy Act, SCIDSA, Texas Medical Records Privacy Act, etc.
- Industry frameworks—PCI DSS, COBIT, ISO 27001, AICPA Trust Services Criteria (TSCs), etc.
Such extensive coverage means organizations working with sensitive data can demonstrate adherence to several regulatory and security standards at once. This improves compliance efficiency and reduces audit fatigue.
Lastly, a HITRUST certification acts as a competitive differentiator and helps you build trust among patients, business partners, and regulatory bodies. This reduces the overall operational risk for any company operating in the healthcare industry.
HITRUST Requirements
HITRUST requirements are based on the HITRUST CSF. The CSF is organized into 19 different assessment domains that are broken into 135 security controls, each with specific requirements.
These domains include:
- Information protection program
- Endpoint protection
- Portable media security
- Mobile device security
- Wireless security
- Configuration management
- Vulnerability management
- Network protection
- Transmission protection
- Password management
- Access control
- Audit logging and monitoring
- Education, training, and awareness
- Third-party assurance
- Incident management
- Business continuity and disaster recovery
- Risk management
- Physical and environmental security
- Data protection and privacy
Not all organizations are required to adhere to all 19 domains or implement all 135 controls in the HITRUST framework. Instead, they can select from the following levels of implementation based on their needs and regulatory obligations:
- Level 1: HITRUST Essentials, 1-Year (e1) Assessment + Certification—This is a baseline standard that covers the fundamentals of cyber security to fulfill basic HIPAA compliance.
- Level 2: HITRUST Implemented, 1-Year (i1) Validated Assessment + Certification—This is designed for medium-sized organizations facing moderate risk. It requires an external assessor like IS Partners to validate the organization’s compliance.
- Level 3: HITRUST Risk-based, 2-Year (r2) Validated Assessment + Certification—This is meant for large enterprises and requires them to adhere to all 135 HITRUST controls.
For e1 and i1 assessments, control requirements are standardized, providing a clear path to certification with periodic updates to ensure relevance. In contrast, the r2 assessment is based on organizational “scoping factors,” such as the volume of sensitive records handled. Organizations managing under 10 million records need about 300 controls, 10–60 million records require 375+ controls, and over 60 million records need around 450+ controls.
r2 assessments are complex to handle. Working with IS Partners helps you make sure you’re looking at all factors and analyzing your organization’s risk exposure correctly.
Our external assessors help you identify applicable controls, perform a gap analysis, and implement all necessary solutions. This way, you avoid common pitfalls and make sure no risk factors, regulatory requirements, or issues are overlooked.
Secure and Maintain HITRUST Compliance With IS Partners
HITRUST is the gold standard for security governance, particularly in healthcare, but achieving certification can be a daunting task. The complexity of the framework and the extensive control requirements often leave organizations unsure of where to begin or how to ensure compliance.
That’s where IS Partners comes in. Our certified external assessors have over two decades of experience guiding organizations through the HITRUST certification process. We help by:
- Identifying applicable controls based on your specific operational environment
- Refining policies and procedures to meet the required maturity levels for certification
- Implementing key security measures to align with HITRUST standards
- Providing ongoing guidance to maintain compliance as requirements evolve
What Should You Do Next?
If your organization is pursuing HITRUST certification, here’s what you should do next:
Assess your current security posture to identify compliance gaps.
Develop and document security policies and procedures to establish a strong foundation.
Collaborate with IS Partners to streamline the certification process and ensure success
HITRUST compliance doesn’t have to be overwhelming. Let IS Partners help you achieve and maintain certification with confidence. Schedule a consultation today!