Threats and attacks are always evolving. That’s why staying on top of cybersecurity requires continual vigilance, updating, and enhancement. Today’s businesses in the health care industry, finance, and others that handle sensitive data know that ensuring security for their organization is a crucial, non-stop job.
We already know that the HITRUST® approach is focused on continual improvement. But it’s not always clear how this ongoing growth is actuated. The HITRUST Maturity Model is built into the HITRUST assessment and certification process precisely for this reason.
The HITRUST CSF® was designed as a unified framework to make IT security clearer and streamline the process of achieving and certifying compliance. Using the maturity model, based on Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) model developed by NIST, the HITRUST CSF also works to strengthen security controls over time.
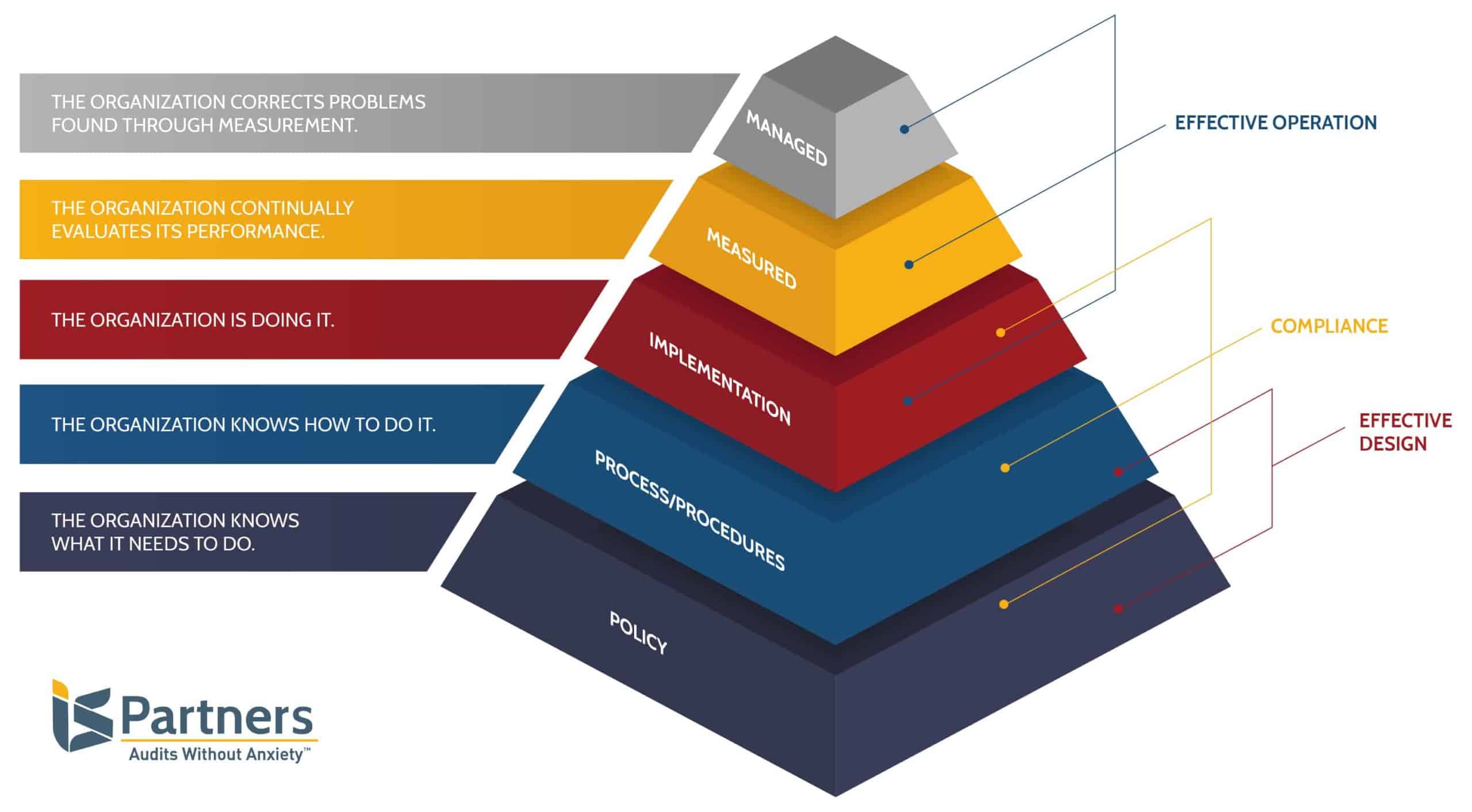
Policy – The organization knows what it needs to do.
Process/Procedures – The organization knows how to do it.
Implementation – The organization is doing it.
Measured – The organization continually evaluates its performance.
Managed – The organization corrects problems found through measurement and steps are taken to mitigate emerging risks.
In this model, you can see how each level builds upon the foundation of the one below it. Like PRISMA, the HITRUST model’s lowest two levels show design effectiveness. The first three indicate compliance. Then, the highest three levels demonstrate operational effectiveness of a given control.
What is the HITRUST CSF Maturity Model?
How the HITRUST Maturity Levels Drive Improvement
Organizations utilizing the HITRUST CSF to guide their compliance operations are able to use the maturity model for benchmarking throughout the security lifecycle and the certification process. Let’s take a closer look at how this applies to each step towards certification.
- Readiness – during the HITRUST readiness phase, the organization compares its existing controls to the five maturity levels to assess its current performance.
- Gap Analysis – by analyzing the difference between current performance and up-to-date certification requirements, as well as the organization’s security goals, gap analysis makes remediation possible. Together with the HITRUST Authorized External Assessor, the organization develops a remediation plan, identifying ways to strengthen their information security environment and risk mitigation controls.
- Validated Assessment – during the validation phase, the organization’s security controls are scored against the maturity model. The assessor validates a set of controls within the scope according to its level of compliance with each HITRUST CSF maturity level. The validated report will also give advice for improvement.
- Quality Assurance Review – The HITRUST Quality Assurance reviewer sums up the average scores of controls in each domain, compares this total to the HITRUST scoring rubric to find the maturity level rating, then quantifies the maturity levels to score the validated assessment.
- Certification – Not only does the maturity model provide the basis for the scoring rubric which determines if HITRUST certification will be issued, it lays out a distinct path towards improvement. For example, if the domain is currently in the Procedures level, the organization knows that it should be working towards the Implemented level.
- Interim Assessment – After one year, an external assessor will review the organization’s certification status. This includes verifying the maturity level and scores of a subset of controls.
- Recertification – After two years, HITRUST certification expires. Recertification will include re-evaluating the maturity of security controls within the scope and assessors will be looking for signs of progress toward stronger maturity levels.
At each step in the process, organizations are provided with guidance on how to increase security in the form of prescriptive, illustrative procedures for each control requirement.
How Control Maturity Ensures Data Security
With the HITRUST Maturity Model, each level builds on the previous one in a cycle of ongoing improvement. And it is precisely this cyclical nature that makes an information security management system successful. In fact, HITRUST has measured the effectiveness of its approach.
In a report published by HITRUST in 2019, assessment data compiled over the past decade showed control maturity provides the best assurance possible. They found that organizations with more mature information security controls are less likely to experience a breach. Plus, these mature information protection programs are better equipped to contain and mitigate the damage in case an attack does occur. This is evidence that controls with high-level maturity are less likely to fail than those implemented badly.
By assessing the maturity of the organization’s information protection program using a comprehensive framework and standardized methods, HITRUST provides the most accurate verification of its risk profile.
How Combining ISCM & the HITRUST CSF Strengthens Risk Management
Other studies have tried to quantify this advantage. One found that organizations with the highest level of maturity and an information security continuous monitoring (ISCM) program suffer 50% less breaches. In fact, the HITRUST Assurance Program and ISCMs go hand-in-hand; both are focused on continual improvement.
Organizations with an ISCM program, and guided by the HITRUST CSF, are continually engaged in assessing the status of information security controls. This ongoing measurement is performed in order to strengthen controls and raise their maturity level. Yet, there are a number of other valuable advantages of combining these two forces that we should note:
- Decisionmakers gain a nearly real-time vision of their risk posture.
- Organizations are able to plan better for risk-based decisions.
- It becomes easier to prioritize remediation activities and develop corrective action plans.
- It’s possible to decrease the time, effort, and expense of maintaining compliance and achieving recertification.
- This type of robust continuous monitoring program bolsters trust among stakeholders.
- It provides a greater level of assurance that best practices are in place now and will be in the future.
See any terms that confuse you? Check out our HITRUST Glossary.
Assurance Made Easy – I.S. Partners
Our motto is “Audits Without Anxiety,” and we mean it! Don’t get overwhelmed by compliance requirements or the assessment process; our team is here to help. Contact I.S. Partners to discuss the challenges that your organization faces and start building a plan for success.




