What’s the Difference Between HITRUST and SOC 2?
HITRUST Certification is a high-assurance certification for healthcare organizations that are legally required to comply with healthcare regulations (such as HIPAA, for example). At the same time, System and Organization Controls 2 (SOC 2) is a lower-assurance attestation for organizations that provide services and need to verify their security controls to customers and prospects.
By the end of this article, businesses will be equipped with the clarity necessary to choose the optimal compliance pathway suited to their specific requirements.
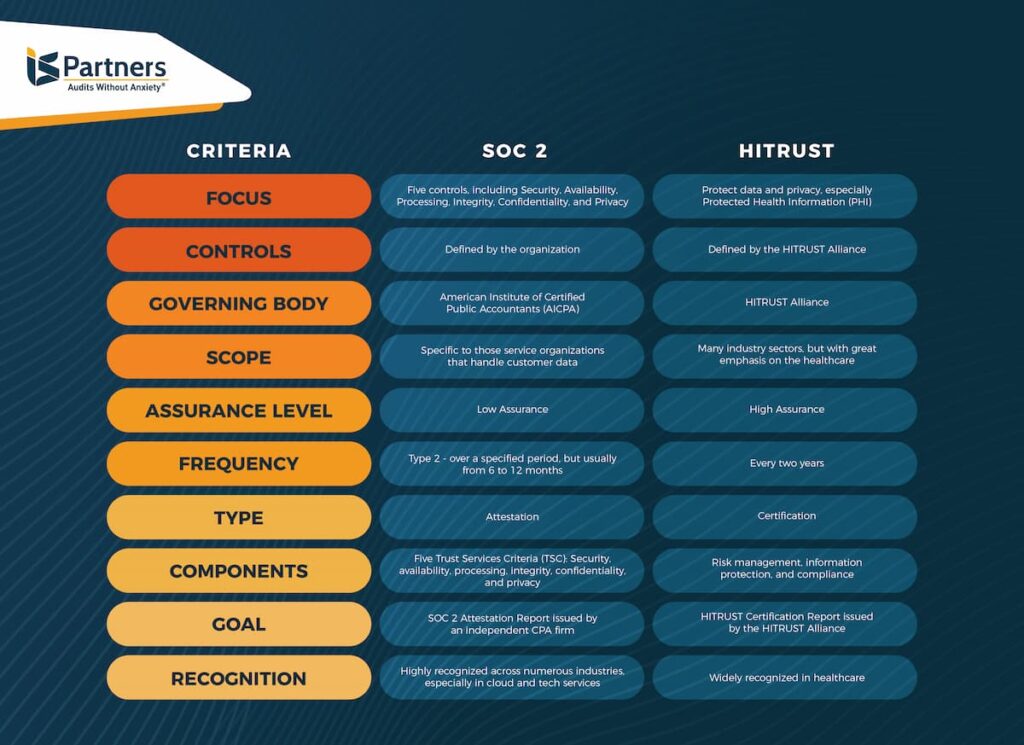
The table below shows the comprehensive difference between HITRUST and SOC 2.
| CRITERIA | SOC 2 | HITRUST |
| FOCUS | Five controls, including Security, Availability, Processing, Integrity, Confidentiality, and Privacy | Protect data and privacy, especially Protected Health Information (PHI) |
| CONTROLS | Defined by the organization | Defined by the HITRUST Alliance |
| GOVERNING BODY | American Institute of Certified Public Accountants (AICPA) | HITRUST Alliance |
| SCOPE | Specific to those service organizations that handle customer data | Many industry sectors, but with great emphasis on the healthcare |
| ASSURANCE LEVEL | Low Assurance | High Assurance |
| FREQUENCY | Type 2 – over a specified period, but usually from 6 to 12 months | Every two years |
| TYPE | Attestation | Certification |
| COMPONENTS | Five Trust Services Criteria (TSC): Security, availability, processing, integrity, confidentiality, and privacy | Risk management, information protection, and compliance |
| GOAL | SOC 2 Attestation Report issued by an independent CPA firm | HITRUST Certification Report issued by the HITRUST Alliance |
| RECOGNITION | Highly recognized across numerous industries, especially in cloud and tech services. | Widely recognized in healthcare. |
Defining assurance levels:
- High assurance: High assurance assessments are the most rigorous and provide the highest confidence level. Independent third-party assessors perform them and thoroughly review the organization’s security controls and processes.
- Moderate assurance: Moderate assurance assessments are less rigorous than high assurance assessments but still provide reasonable confidence. They are typically performed by internal auditors or third-party assessors who are less independent than high-assurance assessors.
- Low assurance: Low assurance assessments are the least rigorous and provide the lowest level of confidence. They are typically performed by the organization itself or by third-party assessors who are not independent.
HITRUST vs SOC 2: Origin and Development
HITRUST stands for Health Information Trust Alliance, and HITRUST refers to the HITRUST framework developed by the HITRUST Alliance, a non-profit organization founded in 2007. The purpose is to champion programs that protect critical information and manage information security risks for organizations across all industry sectors, including third-party supply chains.
However, HITRUST primarily addresses organizations that create, access, exchange, or store Protected Health Information (PHI). According to Daniel Nutkis, CEO of HITRUST Alliance, LLC, HITRUST has become the most widely adopted compliance standard in the U.S. healthcare industry.
The American Institute of Certified Public Accountants (AICPA) first launched Service Organization Control 2 (SOC 2) in 2010 and updated in 2016. It was aimed at providing information on controls and processes at a service organization, together with the independent opinion of the service auditor. Moreover, SOC 2 is virtually applicable for both regulatory and non-regulatory purposes across business sectors and various industries. More importantly, it covers business areas outside of the financial reporting.
HITRUST vs SOC 2: The Vital Difference
The vital difference between SOC 2 and HITRUST standards is that HITRUST is a certification, whereas SOC 2 is an attestation report.
HITRUST issues HITRUST certifications based on its established guidelines and policies. In addition, HITRUST initiates a program to perform HITRUST assessment and issue certification reports. Approved HITRUST assessors can assess an organization’s security controls in connection with an organization’s application for HITRUST certification.
Within a HITRUST report, the organization is management must submit a Letter of Representation rather than a management assertation inscribed within a SOC 2 report. The Letter of Representation is included in a SOC 2 report but not in a final report.
HITRUST assessors generate a final score based on the conducted assessment. The assessor may be a CPA firm but is not required to be. After that, assessors or the CPA firm present their opinion in the certification letter – namely, Letter of Validation or Letter of Certification.
HITRUST assessments are scored against the five levels of the PRISMA-based maturity model.
1. Policy: requires security processes and implementation requirements to be outlined for employees.
2. Process/Procedures: demands that the procedures for implementing security measures are documented and communicated to the individuals who must follow them.
3. Implementation – checks that the organization is implementing all the elements related to security controls.
4. Measured – highlights the importance of gauging performance and testing the effectiveness of controls.
5. Managed – asks the organization to identify problems and address emerging threats.
The HITRUST framework and the SOC 2 reporting model are complementary since both are done through the efficient assessment of security policies and implemented controls.
The validity of HITRUST certification is two years. However, the interim testing is performed within a year.
On the contrary, the SOC 2 attestation report provides assurance regarding the effectiveness of security controls in place at a service organization. These controls are relevant to the availability, security, or processing integrity of a system utilized to process a client’s information, privacy, or confidentiality of such information.
SOC 2 report can be used for third-party risk management, internal or external auditors, or valuable to third-party customers, regulators, or business partners.
Furthermore, SOC 2 attestation reports are completed every year and may go on from one to three months from the completion to the delivery of the report.
SOC 2 vs HITRUST: Mapping Options
Before understanding the mapping options, we need to comprehend AICPA’s Trust Services Criteria (TSC) framework and its Trust Services Principles (TSP), which are listed below:
1. Security: Prevent unauthorized data disclosure
2. Availability: Ensure accessibility to all systems and resources all the time
3. Process Integrity: Complete and authorize all processes on time
4. Confidentiality: Safeguard legally protected information against data breaches
5. Privacy: Protect Personally Identifiable Information in the face of security incidents
A service organization can undergo a SOC 2 examination of any one or all five trust services principles. For example, some SAAS providers may need to address system availability, security, and integrity, but they might not have privacy or confidentiality concerns. Healthcare organizations, on the other hand, must comply with privacy and confidentiality regulations.
Mapping HITRUST criteria in the TSC’s criteria can help service auditors acquire efficiencies by developing audit procedures. Service auditors can use these audit procedures to assess and opine on the design and reliability of controls to fulfill both sets of criteria.
In addition, mapping can reduce the inefficiencies that could occur by performing the assessment. It is conducted to obtain evidence regarding whether controls in service organizations have been designed suitably and operated reliably. Doing so can help meet HITRUST criteria and a separate set of procedures conducted to determine whether the control in organizations has been designed appropriately and operated effectively to fulfill the applicable TSC.
Although mapping is not compulsory in SOC 2 + HITRUST audit report, service auditors can use it when giving opinions on all the HITRUST controls or only those controls required for HITRUST certification. In addition, mapping determines HITRUST criteria that are closely aligned with applicable trust services criteria. Furthermore, leveraging a mapping can help achieve significant efficiencies in planning and performing the SOC 2 + HITRUST engagement.
Assessors should identify and test the security controls that fulfill the criteria explained by the applicable HITRUST and trust services criteria.
Understanding the Essentials of SOC 2 Compliance and HITRUST Standards
Choosing between SOC 2 compliance and HITRUST standards is challenging for any organization. Both SOC 2 and HITRUST help verify an organization’s ability to show adequate security and privacy measures that align with specific trust services criteria set forth by professional auditing bodies such as AICPA.
These regulatory standards have complex features and requirements. Therefore, their complete understanding requires deep research. More importantly, organizations need expert guidance to map out each service included in a SOC report or audit the security measures of an organization against the HITRUST framework.
At IS Partners, we prioritize security, offering comprehensive audits SOC can count on and ensuring your privacy measures adhere to stringent SOC 2 and/or HITRUST criteria. With our detailed SOC 2 services and HITRUST reports, your organization can confidently navigate the compliance journey, secure in the knowledge that our team of specialists is with you every step of the way.
HITRUST + SOC Compliance: A Detailed Overview
Understanding the difference between HITRUST and SOC compliance is fundamental in the digital compliance world. A HITRUST assessment provides a comprehensive technical report outlining a company’s security and risk management.
Likewise, HITRUST audit requires a detailed examination of the organization’s security controls, unlike a basic security report. On the other hand, SOC 2 purely addresses the compliance requirements of service providers handling the data of the consumers. A collection of SOC 2 reports helps maintain the information’s confidentiality, integrity, and availability.
Another difference in a HITRUST vs SOC 2 debate is scope. A HITRUST report reaps the benefit of including HIPAA and NIST controls, thus having a broader scope. On the other hand, the scope of SOC 2 revolves around the AICPA’s five TSCs. However, security is the only needed TSC for the SOC 2 report.
As per Jyotin Gambhir, Founder at SecureFLO, “HITRUST is a standard for a risk assessment that allows you to cover all your HIPAA controls. HITRUST provides you with a certification. HIPAA does not require a HITRUST certification to show compliance. So you do not need to use HITRUST certification to be HIPAA compliant.”
Comparison of Privacy Measures in HITRUST and SOC 2
HITRUST and SOC 2 have essential roles in enhancing an organization’s cybersecurity with data privacy measures. Security professionals compare them due to their high privacy standards. As professionals at IS Partners, we aim to offer explicit opinions on the practicalities and complexities of HITRUST and SOC 2. When we compile reports about HITRUST and SOC 2, we often discover that both emphasize maintaining privacy and enhancing security measures.
To meet many data privacy requirements, HITRUST helps organizations look at the security controls necessary to operationalize their privacy program and meet needs across all standards and laws. To this end, HITRUST harmonizes multiple standards and frameworks as well as state laws. For example, HITRUST includes the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR) laws.
On the other hand, SOC 2 also ensures data privacy with its robust security principles. SOC 2 framework implements access controls to safeguard against cyber-attacks, unauthorized deletion, misuse, disclosure, and alteration of corporate data.
SOC 2 and HITRUST rely heavily on regular reports to ensure ongoing compliance. The focus remains to manage risk effectively and safeguard privacy. Our report on HITRUST and SOC compliance underlines the importance of security and privacy measures in HITRUST and SOC 2. A comprehensive comparison reveals that, while their methods and objectives may differ, both HITRUST and SOC are committed to minimizing risk and ensuring data privacy.
Comparison of Security Measures in HITRUST and SOC 2
You must fully understand HITRUST and SOC 2 security standards to meet your organization’s security needs. The HITRUST standard not only ensures vital security measures but is instrumental in creating an environment of compliance as it affects audits, reports, and services. On the other hand, SOC, specifically SOC 2, carries weight in promoting security and risk management within an organization.
To attain HITRUST certification, organizations must deploy robust data security measures. To this end, they ensure that their data applications and platforms have the following requirements.
- Show privacy, efficacy, and trusted data security capabilities.
- Have the environment and resources to implement the CIA triad – Data Confidentiality, Integrity, and Availability.
- Must protect sensitive data access and storage.
- Consistently apply and support interoperability to protect newly added IT resources, such as programs or applications.
According to Kevin Scharnhorst, Chief Information Security Officer, Health Catalyst, “Having HITRUST certification instills confidence in data protection and security, which is highly sought-after by hospitals and health systems as they deal with the growing demand for increased data security. Provider organizations must know that their data is secure and protected — and HITRUST certification provides that peace of mind.”
Learning about SOC 2 security measures is also crucial because they present an audit perspective that helps an organization understand and manage risk. The compliance reports generated become invaluable tools for changing security services. A thorough understanding and adherence to HITRUST and SOC 2 becomes necessary for robust security measures and compliance.
Comparison of Compliance Reporting for HITRUST and SOC 2
Information reporting in HITRUST often surpasses the reach of SOC reports, leading to intricate audits that delve deeper than your standard SOC audits.
Moreover, audits and compliance maintenance in SOC 2 is easier than that of HITRUST. It’s significant to understand that while HITRUST underscores the protection of information, SOC 2, on the other hand, banks rely heavily on service controls and reporting transparency.
On April 18, 2023, HITRUST released its global compliance reporting program called “Compliance Insights.” This program streamlines organizations’ compliance reporting and support Microsoft Global Healthcare Compliance Scale Initiative.
Reporting security breaches, conducting risk audits, or even meeting the service standards, HITRUST report and SOC 2 have uniquely varied approaches. Therefore, mastering the complexities of these audits can contribute vastly to ensuring optimal organization security and compliance, tailoring services to meet the desired objectives.
| Feature | HITRUST | SOC 2 |
| Reporting Scope | More comprehensive, covering a broader range of security and compliance requirements | More focused on service controls and reporting transparency |
| Audit Complexity | More complex, requiring a deeper dive into security controls and practices | Less complex, with a more streamlined audit process |
| Focus | Less complex, with a more streamlined audit process | Service controls and reporting transparency |
| Approach | Unique approaches to reporting security breaches, conducting risk audits, and meeting service standards | More standardized approaches to reporting and compliance |
| Benefits | Can help organizations achieve optimal security and compliance, and tailor services to meet desired objectives | Can help organizations improve their security posture and demonstrate their commitment to compliance to customers and other stakeholders |
Factors to Consider When Integrating Both Reports
HITRUST includes controls for HIPAA compliance, whereas SOC does not. Based on that, healthcare organizations would need to choose HITRUST over SOC.
When it comes to HIPAA compliance, both SOC 2 and HITRUST reports have their places. You must consider a few key factors to facilitate the efficient integration of both types of reports within your organization’s structure.
Firstly, understanding the standard business requirements of HITRUST and SOC 2 compliance is paramount. Secondly, assessing the information risk and adhering to security audits will determine the overall security measures for your company. Your services should incorporate these audits to establish a firm grasp of reporting risk and service procedures.
Additionally, the intricacies of reporting should be well addressed as guided by both SOC and HITRUST standards. As audits are repeated periodically, your service must be consistent with the standard operational procedures of SOC and HITRUST.
While the organization relies heavily on the effective integration of information from both reports, it’s equally important to consistently upgrade your services according to the evolving landscape of cybersecurity. Regular audits will ensure compliance and avert potential threats, strengthening your organization’s defensive stance against breaches.
Comparing Reporting Options Between SOC 2 and HITRUST
There are four types of reporting that service organizations can consider.
| Reporting Option | Description |
| SOC 2 Reporting Only | An attestation report that provides assurance about the security, availability, confidentiality, processing integrity, and privacy of a service organization’s system. |
| SOC 2 + HITRUST Reporting | A combined report that provides assurance about the security, availability, confidentiality, processing integrity, and privacy of a service organization’s system, as well as compliance with the HITRUST. |
| HITRUST CERTIFICATION (without a SOC 2 report) | A certification program that assesses an organization’s compliance with HITRUST. |
| SOC 2 + HITRUST audit + HITRUST Certification | Combines a SOC 2 audit and a HITRUST audit, resulting in a SOC 2 report and HITRUST certification. |
We must consider various factors when comparing SOC 2 and HITRUST reporting options. These include the nature of security audits, compliance requirements, and the organization’s information risk profile. Both SOC and HITRUST are pivotal in fortifying an organization’s security posture, as they ensure comprehensive security and privacy measures are in place.
HITRUST reports act like a tailored security guide, focusing on the unique risks associated with health data. SOC 2, on the other hand, yields a broader audit that focuses on a single organization’s services and processes. Both audits provide invaluable services for assessing compliance with industry standards.
Your choice between HITRUST and SOC 2 should reflect your organization’s specific needs and the level of compliance required. Reach out to IS Partners today for expert guidance on HITRUST and SOC 2 compliance.
HITRUST Cost vs SOC 2 Cost
The expenses associated with achieving SOC 2 and SOC 2HITRUST compliance for an organization depend on various factors such as security measures, audits, and information risk management. Assessing the cost of HITRUST certification, you need to factor in a fairly intensive process of meeting robust security requirements, undergoing rigorous audits, producing detailed reports, and constantly monitoring compliance.
Switching focus to SOC 2, organizations are also subject to thorough audits, comprehensive security practices, and in-depth reports to ensure information and risk management meet SOC standards.
However, when choosing between SOC 2 or HITRUST, service organizations consider the price associated with these frameworks. The HITRUST certification might initially seem more expensive due to its extensive criteria, but it can offer broader coverage. On the other hand, the cost efficiency of SOC 2 compliance could appeal to organizations. Whatever the choices are, IS Partners strives to guide clients through their respective information security journeys.
HITRUST + SOC 2: Optimizing Your Compliance Strategy With a Unified Approach
HITRUST and the AICPA collaborated to develop a set of recommendations to simplify the compliance process. Because some service organizations have very specific reporting formats from which they may not deviate, it was essential to implement an internal control reporting structure that is efficient yet flexible. By joining HITRUST and SOC 2, your organization can benefit from some valuable advantages.
What Are the Advantages of Using the HITRUST + SOC 2 Combined Reporting Model?
Mapping the HITRUST framework to the AICPA SOC 2 Trust Principles and Common Criteria is a way to provide a reporting structure that is both efficient and flexible. Under this reporting structure, the HITRUST + SOC 2 report becomes the default method of reporting that meets a broader range of requirements.
Saving on the Time & Expense of Compliance
Carrying out two separate auditing and reporting processes for HITRUST and SOC 2 can take your organization’s time, effort, and resources. The SOC 2 + HITRUST reports are designed to help service organizations that create, handle, store, or transmit PHI to meet their dual reporting requirements.
Because there is some overlap between the two standards, combining the security assessment processes helps save your organization time and money. You can evaluate compliance with controls comprised of both requirements in a single report. This is beneficial for organizations of all sizes, but especially for companies that have thin resources.
Consolidate Audit Resources
Extensive security controls and lengthy documentation are needed to meet SOC 2 and HITRUST compliance. Mapping reveals overlap in HITRUST and SOC 2 controls in multiple areas. Some examples include organizational and management criteria, communications, the design and implementation of controls, monitoring, physical access, systems operations, and change management.
Combining the processes means consolidating audit evidence and reducing the amount of time demanded by internal and external auditors. It’s also likely to help prevent the dreaded audit fatigue.
What Do You Need for SOC 2 + HITRUST Certification?
HITRUST suggests engaging a CPA who also functions as a HITRUST Authorized External Assessor to enjoy the efficiency of satisfying both needs in one step. While an independent CPA can assist with assessing performance using HITRUST criteria, only a HITRUST Authorized External Assessor can guide your organization through the validated assessment and certification process.
Streamline HITRUST Certification & SOC 2 Compliance Today
Want to make regulatory compliance a faster, anxiety-free process for your organization? Schedule a consultation with one of our HITRUST and SOC 2 auditing experts today!
Through years of devoted service and commitment to excellence, IS Partners has earned a reputation of trust and expertise, having successfully completed thousands of SOC 2 Audits and HITRUST Certifications for companies worldwide.
Our team constantly seeks new efficiencies and strategies to save our clients time and effort. Schedule a consultation with one of our HITRUST and SOC 2 auditing experts to determine how we can make regulatory compliance a faster, anxiety-free process for your organization.
FAQs About HITRUST vs SOC 2
Glossary
Availability
Availability is a critical component of the CIA triad and it ensures that all services and resources are always available.
AICPA
The American Institute of Certified Public Accountants (AICPA) promotes accounting and finance worldwide. They also introduced Service Organization Control 2 (SOC 2) in 2010 and updated it in 2016.
CPA Firm
CPA Firm is a licensed agency that conducts SOC 2 audits and issues SOC 2 attestation reports.
Confidentiality
Confidentiality is a security control in the CIA triad whose implementation is necessary to obtain HITRUST certification. Confidentiality prevents the interception of data while it is in transit.
Compliance
Compliance or regulatory compliance is an act of following the international industry standards (e.g., SOC 2, HITRUST, HIPAA, GDPR, etc.) to enhance the organization’s security posture and avoid penalties.
HITRUST
HITRUST stands for Health Information Trust Alliance, and HITRUST refers to the HITRUST framework developed by the HITRUST Alliance, a non-profit organization founded in 2007.
HITRUST Certification
HITRUST Certification is a high-assurance certification for healthcare organizations that are legally required to comply with healthcare regulations (such as HIPAA, for example).
HITRUST Assessment
A HITRUST assessment is a precise audit that analyzes the organization’s compliance with robust security requirements.
Integrity
Integrity is also a security control of the CIA triad, which is essential for HITRUST certification. Integrity security controls ensure that data is not modified, changed, or altered.
Integration
Integration is a security practice that combines HITRUST and SOC 2 reports.
Mapping
Mapping is also a security practice that helps organizations map HITRUST criteria in the TSC’s criteria. Doing so can assist service auditors in acquiring efficiencies by developing audit procedures. In addition, mapping can reduce the inefficiencies that could occur by performing the assessment.
Risk Management
Risk management is a security control that is essential in SOC 2 attestation reports.
SOC 2
AICPA first launched Service Organization Control 2 (SOC 2) in 2010 and was updated in 2016. It was aimed at providing information on controls and processes at a service organization, together with the independent opinion of the service auditor.
SOC 2 Attestation Report
SOC 2 attestation report provides assurance regarding the effectiveness of security controls in place at a service organization. These controls are relevant to the availability, security, or processing integrity of a system utilized to process a client’s information, privacy, or confidentiality of such information.
TSC
Trust Services Criteria (TSC) is AICPA’s framework that features five Trust Services Principles (TSP): Security, Availability, Processing, Integrity, Confidentiality, and Privacy.
References
- HITRUST Alliance, “Making the Move from SOC 2 to HITRUST Easier (and More Advantageous),”
- Health Catalyst, “5 Ways HITRUST Common Security Framework Protects Data,” 2023.