HIPAA: Regulations for the Security & Privacy of Healthcare Information
Enacted by the U.S. Congress in 1996, the Health Insurance Portability and Accountability Act, or HIPAA, was put in place to safeguard electronically protected health information (ePHI). An entity is bound by HIPAA if it functions as a healthcare provider, a healthcare plan, a clearinghouse, or any other type of covered entity that works with confidential electronic data in or related to the healthcare industry. There are two main HIPAA regulations – the Security Rule and Privacy Rule.
HIPAA Security Rule
More specifically, the HIPAA Security Rule protects individuals’ medical records and other personal health information that is created, received, used, and stored. It applies to three different security parameters — physical, technical, and administrative — along with a set of various organizational and document requirements, policies, and procedures with which an organization must comply.
HIPAA Privacy Rule
The HIPAA Privacy Rule, on the other hand, aims to set boundaries and give individuals’ control over how their personal information is used. Covered entities can use PHI for treatment, payment, and other required operations, while keeping the sensitive data confidential. The Privacy Rule covers physical security and confidentiality of PHI in all forms – electronic, paper, and oral.
Get more information about HIPAA-Compliant Telehealth and Avoiding Violations During the Pandemic.
HITRUST: Framework-Based Approach to HIPAA Compliance & More
Founded in 2007, HITRUST® is a collaborative body of leaders in healthcare, technology, business and information security. The HITRUST CSF® evolved from and incorporates HIPAA regulations; it is a comprehensive framework designed to help organizations from all sectors – including, but not exclusive to healthcare – effectively manage data, information risk, and compliance.
The HITRUST CSF works on the principle that information security is an integral part of the expanding use of technology – in business and healthcare – to collect, organize, and store electronic data. It gathers all updates from various federal entities regulating information security, including HIPAA. The HITRUST CSF provides anyone handling sensitive data the quintessential framework a comprehensive base of information, controls, and tools to achieve high levels of security to reach and maintain compliance with confidence and clarity.
Featuring 19 control categories and three levels of implementation, the HITRUST CSF covers a wide range of security measures, from network protection and vulnerability management to physical and environmental security. The three levels of implementation categorize each control by the amount of associated risk: organizational risk, regulatory risk, and system risk.
Not only is the HITRUST CSF comprehensive, but it is also prescriptive and corrective, offering ways to make necessary corrections and maintain the HITRUST CSF Certification. As a verified demonstration of compliance, HITRUST certification also shows your organization’s commitment to the highest standards of information security.
What Is the Difference Between HIPAA and HITRUST?
Very simply put, HIPAA is an act that details the standards of compliance, while HITRUST CSF is a workable framework that helps you achieve compliance. Let’s take a closer look and compare the advantages of HITRUST CSF Certification to HIPAA auditing.
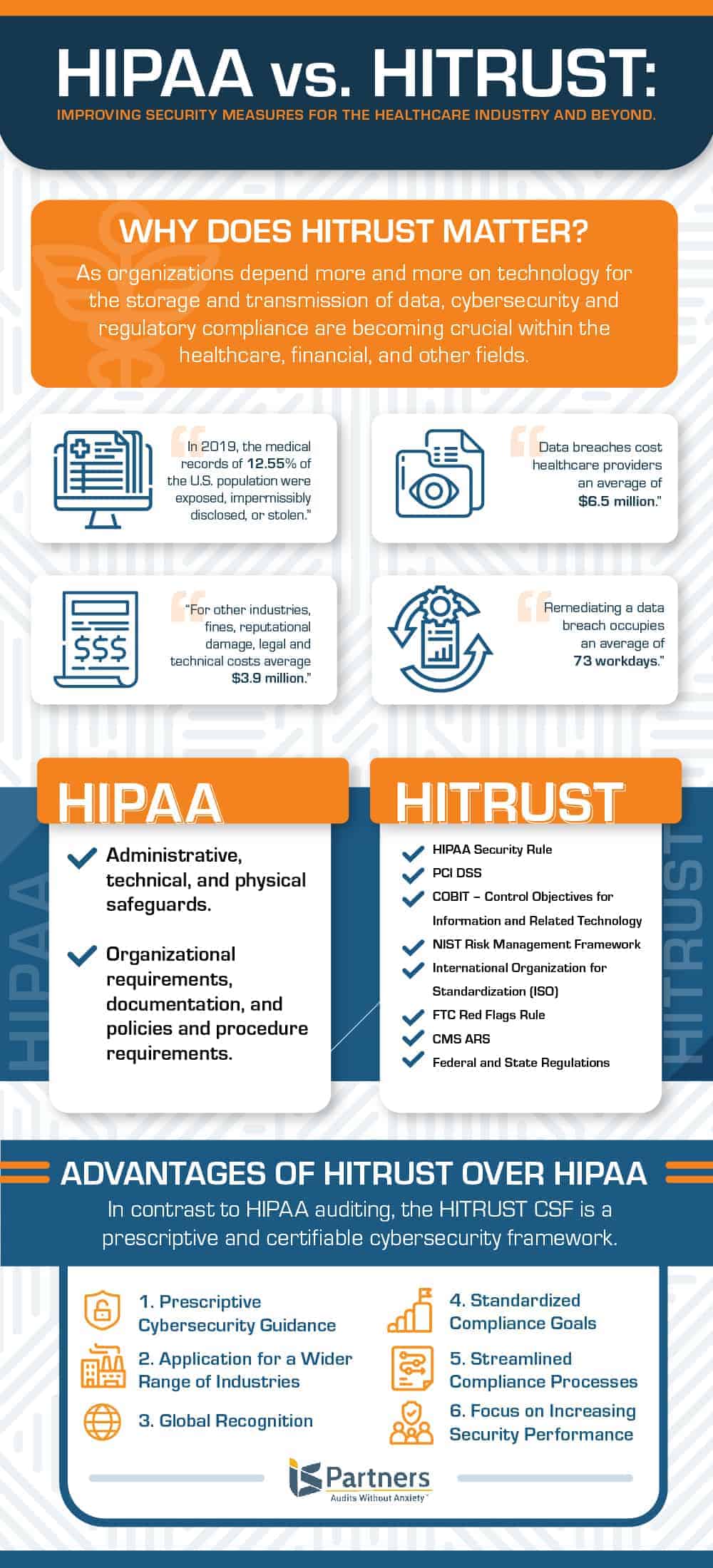
1. Prescriptive Cybersecurity Guidance
HITRUST uses HIPAA as part of its base and builds upon it within the structure of the HITRUST CSF. HITRUST takes HIPAA, which is a non-standardized framework that offers no prescriptive measures, and expands the underlying principles to create a prescriptive and certifiable framework.
2. Application for a Wider Range of Industries
HITRUST is trusted by healthcare providers, financial institutions, and more, which is why the HITRUST CSF Certification is so valuable. Where HIPAA is applicable only to the medical and healthcare industry, HITRUST is recognized throughout many industries.
3. Global Recognition
HITRUST is globally recognized; HIPAA only applies to covered entities and business associates operating within the United States.
4. Standardized Compliance Goals
HITRUST works to harmonize the various regulatory standards and frameworks set up by federal agencies. It gathers information from entities like HIPAA, HITECH, NIST, ISO, COBIT, and PCI to create a comprehensive, standardized view of information security and privacy needs.
5. Streamlined Compliance Processes
This harmony created by the HITRUST CSF means that covered entities and business associates can save on the time, effort, and expense linked to regulatory compliance. They can rely on just one assessment process and certification to meet their compliance obligations imposed by multiple different standards, like those mentioned above.
6. Focus on Increasing Security Performance
The HITRUST approach aims for continual improvement; based on the HITRUST CSF Maturity Model, assessment scoring encourages organizations to progress from the policy level toward procedures, implementation, measurement, and management. A large part of the value of the HITRUST CSF certification comes from the rigorous commitment of you and your staff.
HIPAA, on the other hand, is more punitive than reward-based, defining penalties for data breaches. A simple HIPAA audit typically requires less effort and resources, but it doesn’t offer the same benefits as HITRUST CSF Certification.
Get extra guidance with our HITRUST Glossary.
An Outside Assessment Firm to Help You Navigate HIPAA & HITRUST
At I.S. Partners, LLC., we help our clients to understand the differences between HIPAA and HITRUST and decide which one is right for their organization. We can help your organization prepare for the appropriate assessments for either framework.
Call us today at 215-675-1400 so we can work with you and your IT team to create a safe and compliant environment to protect your organization’s sensitive electronic data.




