Automation has been creeping into various business processes over the past decade and being increasingly used to improve efficiency and accuracy; cybersecurity compliance is no different. In the past, compliance efforts were largely manual operations and time-consuming, making it difficult to keep up with the rapidly changing landscape of cybersecurity threats. Automation has helped to change that by providing a way to automate repetitive tasks and quickly respond to new threats.
Benefits of Automating Compliance Processes
As you can imagine, there are a number of benefits that automation has brought to cybersecurity compliance. And as the technology of artificial intelligence and machine learning continues to evolve, we expect the advantages to become even greater.
- Greater Accuracy – First, it can help to improve accuracy by automating tasks that are prone to human error. For example, if a security team is manually scanning for vulnerabilities in their network, they may miss some that could be exploited by attackers. By using an automated vulnerability scanning tool, they can be sure that all potential vulnerabilities are being identified.
- Faster Reaction Time – Second, automation can help to speed up the compliance process by eliminating the need for manual tasks and the reliance on man-hours. This is particularly important in fast-moving environments where new threats can emerge at any time. By automating tasks—like incident response and patch management—security teams can react more quickly to new threats and reduce the risk of an attack becoming a data breach.
- Streamlined Data Collection – Automation improves the accuracy of compliance-related data collection and analysis. For your compliance team and your company, software-based compliance solutions replace those old spreadsheets, creating a single source of truth. This means that IT security teams have a unified repository for all of your compliance data and no longer need to worry about making judgments based on information that is insufficient, out-of-date, or inaccurate.
- Centralized Compliance Resources – Similarly, automation helps keep track of all compliance activity in one location, including regulations, policies, record, contracts, and agreements that may have previously been stored in word documents or web browser bookmarks.
- Consistent Workflow – Workflow automation for compliance, which enables you to program software to follow rules-based instructions to complete an entire task without human intervention, is one technique to automate a compliance process. Another example is the use of software to automatically renew and track overdue items rather than requiring you to update tasks manually, and it only notifies you in accordance with your pre-set rules.
- Increased Focus on Critical Tasks – Automation is critical for ongoing improvement of cybersecurity compliance programs. In the context of cybersecurity compliance, automation can be used to streamline a variety of tasks, including asset inventory, vulnerability management, and patch management. Automating these tasks can help to improve the efficiency of the compliance process and free up resources that can be better spent on more strategic initiatives.
- Lower Compliance Risk – Utilizing dedicated software platforms assists businesses in maintaining compliance and avoiding fines and other penalties for non-compliance. For example, they can clearly see their compliance status and risk stance from a central dashboard in real-time.
- Decreased Compliance Costs – The majority of CISOs have needed to reduce spending for the upcoming fiscal year resulting in a minimal investment in compliance, governance, and risk assessment tools. Reduced budget has also limited corporate security spending on more advanced threat-intelligence improvements and behavioral analytics. Yet emerging technologies in the cloud, data analytics, and robotic process automation are helping CISOs reach top cybersecurity investment goals while also cutting costs.
- Reduced Reliance on Cybersecurity Staff – In an industry is experiencing higher demand on skilled professionals within a nationwide labor shortage, computerization is more advantageous than ever. Companies can avoid the problem of a skills scarcity with technologies that analyze hazards in real-time and automate parts of the risk assessment processes. As a result, firms can hire security professionals for jobs that have a higher rate of return, which will significantly lower the demand on current staff and the need to hire additional employees.
- Agile Vendor Governance – We know that third-party providers are a growing threat to cybersecurity and that the best way to mitigate it is through regular vendor risk assessments. With automation, supply chain management and third-party risk management become easier to ensure transparency and accountability. Computer-aided mapping of risks to relevant security regulations, internal stakeholders, and external vendors, makes vendor governance easier to achieve.
Related article: the Rising Cost of Compliance and How to Optimize Efforts.
But Automation Isn’t Enough! Compliance Must be Guided by Skilled Professionals.
While automation is a critical component of an effective compliance program, it is important to remember that compliance is a holistic process that requires the engagement of people, processes, and technology. When all three of these elements are working together, businesses can create a strong foundation for protecting their data and meeting their compliance obligations.
While it is true that software-only compliance platforms help organization documentation and track progress on controls reporting, they don’t check the quality of what your team uploads. It allows your team to check off the boxes as they work, but won’t give them feedback about what is incomplete or incorrect. In this sense, they are more of a receptacle than a service.
When working with a certified CPA firm, they guide your organization through the full security control lifecycle – design, implementation, analysis and assessment, then monitoring. If you choose to work with an automated compliance platform, they really only provide assistance in the monitoring phase.
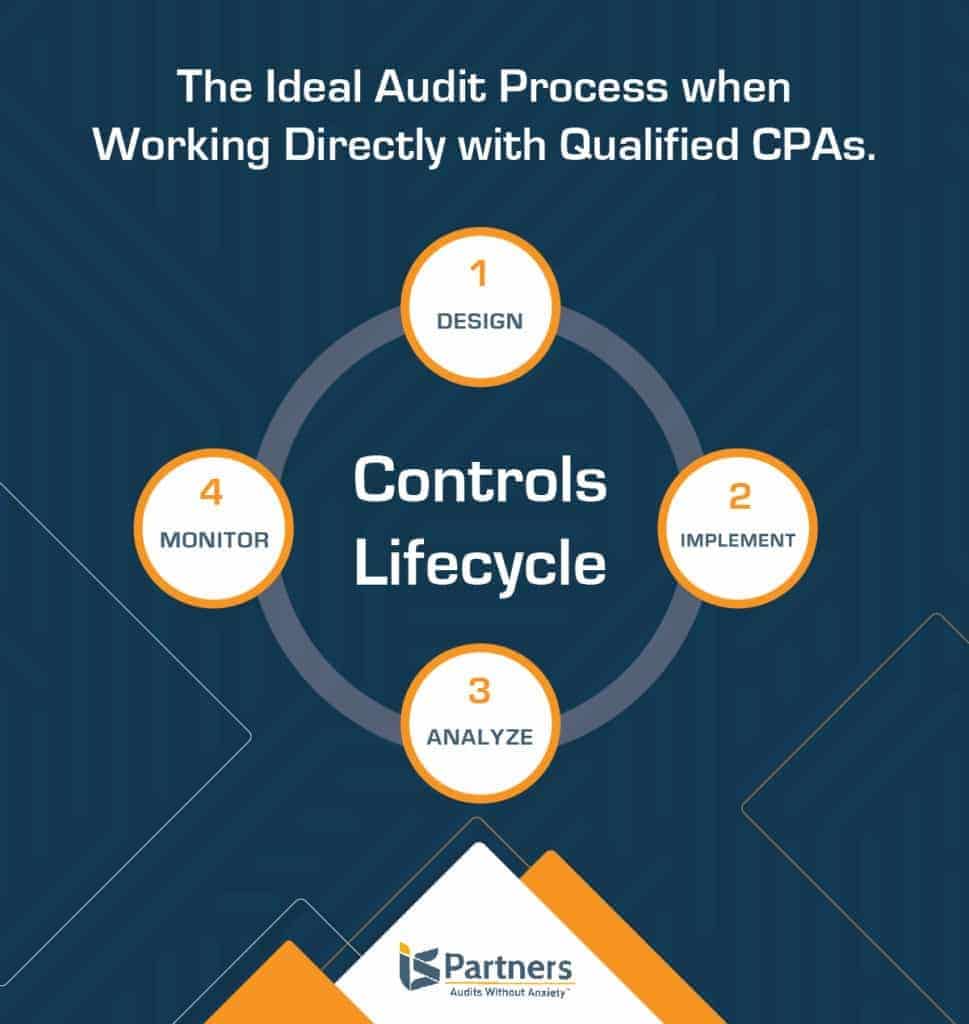
An experienced auditor is needed to fully understand your organization, IT environment, industry, security controls, and compliance requirements. By working directly with an assessment firm, your compliance process is personalized and your time is optimized. This is particularly true when compliance with multiple regulations is required. Your auditor will map controls, ensure that you only provide evidence once, and combine audit efforts.
Related article: Virtual CISO Services Guide Security Efforts at a Fraction of Hiring Internally.
Compliance success requires more than just the tools. You need a team of security experts and CPAs that is hands-on to get your organization certified. Contact I.S. Partners and our AWA division to learn more about our automated solution that will soon make the auditing process even faster and smoother for all our clients.