Key Takeaways
1. The Trust Services Criteria consist of five different elements: security, availability, processing integrity, confidentiality, and privacy.
2. Licensed auditors use the TSCs as a framework for evaluating a service organization’s security controls.
3. IS Partners, LLC is composed of teams of experts specializing in SOC 2 audits. Our experts can guide you regarding which criteria to focus on.
What Does TSC Mean?
TSC means Trust Services Criteria. This framework was previously known as the Trust Services Principle before 2018.
What is the Trust Services Framework?
The Trust Services framework refers to the auditing system based on the Trust Services Criteria. The TSC is a set of control criteria for assessing and reporting on controls for information and systems.
The Trust Services Framework is basically used as a guide to evaluate a service organization’s security system and capability to protect customer information.
According to the framework’s standards, a robust and effective security system is credible and efficient in protecting information from threats such as breaches. Licensed CPAs use this framework to detect the potential risks in a service organization’s operations and draw possible solutions to preserve security.
Is TSP Different from the TSC?
TSP, or Trust Services Principle, is similar to TSC, or Trust Services Criteria.
A few years ago, the name “Trust Services Principles” for SOC 2 reporting was changed to “Trust Services Criteria.” However, the concept remains the same—offering a framework for assessing the SOC 2 controls related to information and systems and reporting on them.
In addition, the five categories encompassed in the framework remain the same.
What Are the 5 SOC 2 Trust Services Criteria?
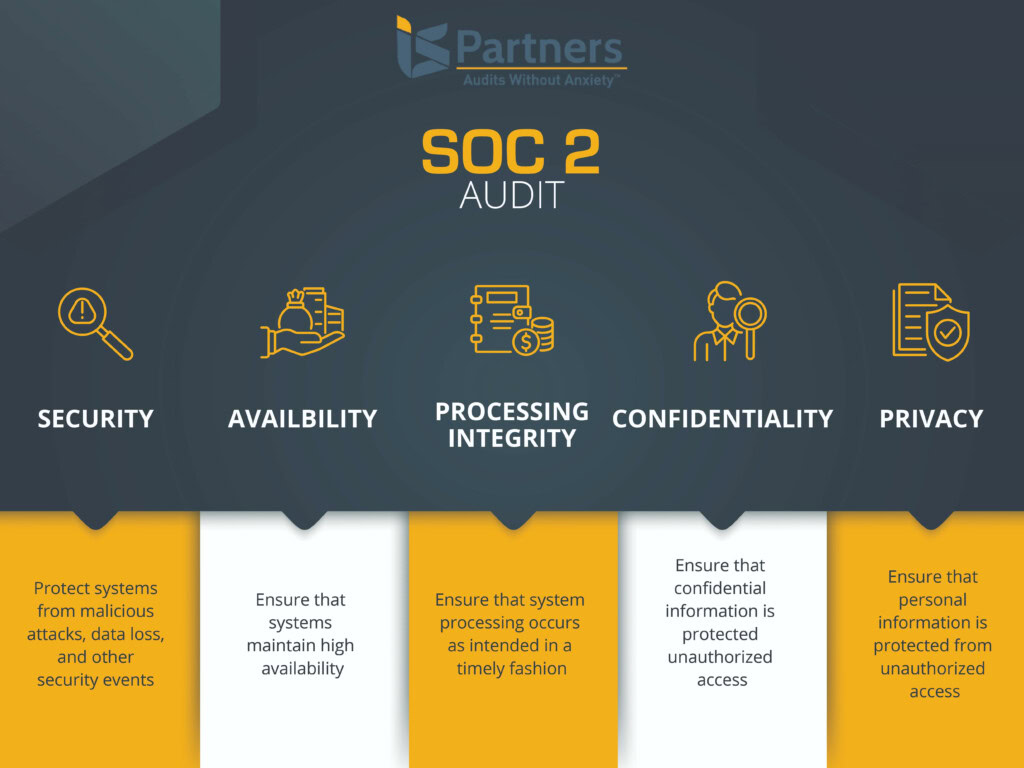
The five TSCs of a SOC 2 audit are security, availability, processing integrity, confidentiality, and privacy. Since December 2018, all SOC 2 audits must comply with these five criteria outlined in TSP Section 100.
Each criterion focuses on a different aspect of information security. Together, they build a framework that effectively protects information flowing through the service organization.
The five Trust Services Criteria are described in detail below.
Security
Security is the most critical criterion among all Trust Services Criteria. Its objectives include ensuring that all data and information are properly processed, transmitted, and disposed of.
The criterion ensures that a service organization’s security system has the correct controls to detect and prevent malicious threats. It also requires a proper recovery plan and an effective system for addressing threats in case breaches occur.
Security controls require the participation of the entire IT department, operations team, and management. Auditors base the evaluation of an organization’s security controls on nine common criteria based on the COSO framework, discussed in the next section.
Availability
All information and computing systems are ready and available for operation and use as needed. The criterion ensures that access, processing, and release of information is secure and fast with the least amount of downtime.
Availability also includes controls on the efficient detection and handling of breaches. The criterion can help organizations handle growing demand and prevent a decline in the efficiency of services.
Processing Integrity
The criterion Processing Integrity focuses on determining if your system works and how accurate the results are based on the objectives. This includes evaluating if the results are complete and free from tampering or omission.
This auditing criterion is commonly fit for financial reporting services and e-commerce companies. Processing Integrity criterion also requires controls for maintaining the correctness of information as it travels along the processing line or gets stored.
Confidentiality
This criterion determines how well a service organization protects information from leaking as it is processed. Confidentiality includes requirements for controls to protect sensitive information entrusted to your business by customers.
Under this criterion, organizations must clearly define access limitations of involved team members and customers. It also includes having proper procedures for disposing of confidential information if the contract with the customer is terminated.
Privacy
The Privacy criteria explain that personally identifiable information collected, used, retained, stored, disclosed, or disposed of must maintain privacy and ensure compliance with AICPA’s regulations. The criterion requires organizations to have internal controls to prevent unauthorized access and breaches.
How Does the TSC Integrate the COSO Framework?
Another vital change is the integration of the control criteria with the 2013 COSO Framework. The COSO stands for the Committee of Sponsoring Organizations of the Treadway Commission, and the body set out to provide a framework for publicly traded companies to rigorously assess and report on the design and operating effectiveness of their internal controls each year.
This framework was integrated into SOC 2 reporting to expand the assessment environment. The 2013 COSO is used to assess internal controls’ design, implementation, and maintenance and evaluate their effectiveness.
Since integrating into the TSC, the COSO Framework criteria are now termed common criteria or the CC series. These criteria are integrated into the security principle of the TSC.
Five of the nine common criteria from the COSO framework are considered essential to achieve security. Below are the five SOC 2 common criteria:
- Control Environment – The control environment should be committed to ethical values, integrity, and competency and enforce accountability. It should also have appropriate policies and guidelines for structure, authority, and responsibility.
- Risk Assessment – Risk assessments must have suitable objectives. Under this criteria, an organization must have a clear plan on how to identify and evaluate potential risks along with their potential impact on the business.
- Information and Communication – This set of controls governs the selection of relevant information and the appropriateness of internal and external communication. This set of controls includes the need to establish clear communication channels with all members of the organization and external stakeholders to transmit responsibilities and data efficiently.
- Monitoring Activities – These outline the need to prepare and conduct ongoing or separate assessments and evaluate issues and deficiencies identified by assessments. This control requires organizations to have a clear method to determine if the security system is working properly.
- Existing Control Activities – These controls cover the selection and development of control activities and general technology and the deployment of activities through policies and procedures.
The list of SOC 2 common criteria summarizes the overlap between the different TSCs. This aspect makes the security criteria necessary for all SOC 2 audits. In addition to the five key criteria mentioned, four more criteria are considered for security.
- System Operations – The way that service organizations handle the operation of their systems in order to monitor, detect, and mitigate security incidents.
- Logical and Physical Access Controls – The ways that service organizations implement logical and physical access controls that serve to prevent unauthorized access and protect data assets.
- Change Management – How service organizations evaluate and determine necessary changes in infrastructure, data, software, and procedures, allowing them to make and prevent unauthorized changes securely.
- Risk Mitigation – How service organizations identify, choose, and develop risk mitigation strategies for risks involving vendors, business partners, and any other possible disruptions.
These additional criteria are supplemental to improving an organization’s internal controls.
Are All Trust Service Principles in SOC 2 Mandatory?
No, businesses are not necessarily required to address each of the five of the Trust Services Criteria. Reviews and audits may be limited to the relevant principles if a business performs an outsourced service.
Among the five SOC 2 principles, only the security criterion is mandatory. Your organization will need to choose different criteria for the audit to focus on based on the services you provide.
Which Trust Services Criteria Should You Include in Your SOC 2 Audit?
While all the Trust Service Criteria are critical in holistically ensuring security controls, not all organizations can prioritize all five simultaneously. As such, you can choose other criteria besides security to be the point of focus of a SOC 2 audit.
When choosing which criteria to focus on, your organization must consider the following factors:
- Industry requirements
- Customer needs and expectations
- Business objectives
- Legal requirements
- Potential threats to business
The best way to determine which criteria to focus on is to seek the advice of a licensed CPA. They will be able to thoroughly assess your business operation and suggest which criteria your current policies and systems require.
To help you trim down your choices, here is a list of business industries suggested to focus on a particular criteria for a SOC 2 audit:
- Availability
- Telecommunication companies
- E-commerce platforms and online marketplaces
- Cloud service providers
- Financial institutions providing online banking and trading services
- Healthcare organizations
- Processing Integrity
- Financial institutions required to ensure accurate and timely transactions
- Payment processors
- Data processing companies
- Logistics and supply chain management companies
- Government agencies handling sensitive information
- Confidentiality
- Legal firms
- Consulting firms
- Research and development companies
- Healthcare organizations
- Tech companies
- Privacy
- Tech companies
- Healthcare organizations
- E-commerce platforms
- Financial institutions
- Government agencies
This non-exhaustive list shows how one type of organization may need multiple points of focus to secure data handling.
Contact I.S. Parnters, LLC today and let our experts guide you through which criteria to focus on.
Why Are the Trust Services Criteria and 2013 COSO Framework Important to SOC Reporting?
Working with service organizations has become a standard operating procedure for most businesses. Even smaller companies often outsource some aspects of their business for matters like cloud storage or payroll, so everyone using these valuable resources must protect their vital and confidential information and technology.
The TSC offers CIOs and other business leaders a clear set of guidelines to work confidently with service organizations while protecting their interests.
How Is Data Covered by the Trust Service Criteria Categorized?
The data that is handled under the TSC can basically be broken into three broad categories based on how important it is to safeguard that data. The more important it is to protect data, the stricter its categorization.
We break the categories into three basic levels:
- Public – Public data is any data that is, or can safely be, publicly known. Would you publish it on a postcard? This is public data. Examples can include your address, store hours, the identity of your CEO, and the like. There is no obligation to make any special effort to protect this data, as it is readily available.
- Internal – Internal data is data that should not be spread outside the internal workings of the company. This data, if leaked, could cause moderate risk or damage to the business. Examples of internal data include company handbooks and policies, encryption keys, and API keys. This information could be used in a harmful way, but the harm that can be done is limited.
- Confidential – Confidential data is the data that, if it were released improperly, could cause the company severe harm. This harm could be financial, or it could be to the reputation of the company. Confidential data include credit card information, prospective customer lists, data from inside your CRM, customer passwords, financial reports, and confidential data entrusted to you by your customers.
Some companies create additional data categories, such as Restricted categories that handle information like credit card numbers. However, the more complex a data categorization system is, the better the chances that data will be categorized incorrectly.
While there’s not a lot of risk in categorizing something that is public data as internal, it can be very damaging to apply a less stringent label to a piece of data that could do a lot of harm if it got out into the wild.
Define How the Trust Services Criteria Affect Your Business
If you are a budding business and do not know which criteria to focus on, you need an expert auditor. A licensed CPA will guide you and correctly determine which criteria are best for your business.
Contact IS Partners, LLC to work with an experienced CPA to define how the TSCs impact your business and prepare for a successful SOC audit. Our team specializes in conducting SOC 2 audits for different businesses with years of experience in successfully guiding organizations.
This post was originally published on December 10, 2015, and has since been modified multiple times to reflect the most up-to-date information.