In today’s environment fraught with cybercrime, hackers, and malicious attacks, no organization can be too vigilant. This is why risk management has become a crucial measure in protecting sensitive information.
Given the circumstances of 2020, companies operating in every industry have come to rely more and more on cybersecurity frameworks for guidance in managing IT-related risks. Tools, like NIST risk assessments, help ensure the security of the organization’s network, applications, vendor services, and customer data.
The NIST Cybersecurity Framework (CSF) provides an outline of the necessary security processes and controls. It was designed to be agile enough that businesses of any size, and operating in virtually any industry, can apply its principles. With the help of the NIST framework, organizations can work to continually improve security measures.
Read about NIST SP 800-53 and How to Maintain Compliance.
NIST RMF: Risk Management Framework
More specifically, the NIST Risk Management Framework (RMF) is a comprehensive guide for applying risk management best practices in the current period. Plus, it also promotes improvement and better management of information security risk over time by combining the RMF with the system development lifecycle. Each task in the RMF aligns with sections of the NIST CSF, facilitating an easy transition to the broader framework.
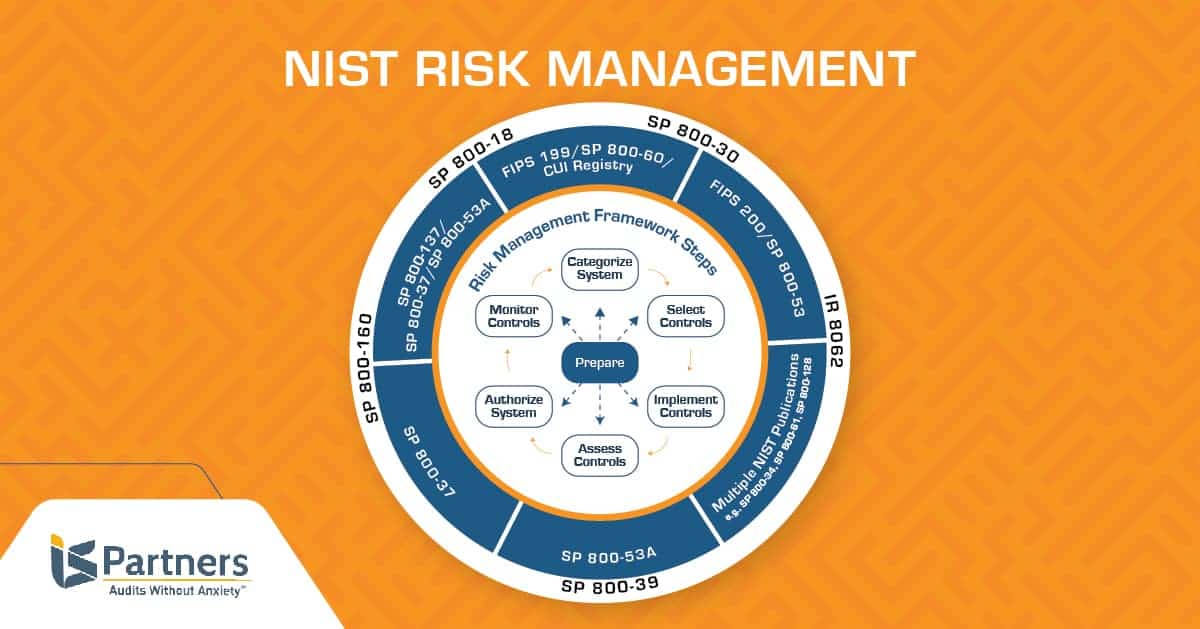
The NIST Risk Assessment Procedure
According to NIST Guide for Conducting Risk Assessment, the risk assessment process should include three phases: preparation, assessment, and maintenance. In fact, the RMF lays out these seven steps:
- Prepare – The organization reviews essential internal activities at the organizational, mission and business process, and information system levels to prepare the organization to improve the management of security and privacy risks.
- Categorize – Determine the criticality of the information and system according to the potential worst-case scenario, potential damage to the organization, business functions, and system.
- Select – Identify the security controls using categorization output from the first step and the appropriate baseline. Then, apply guidance as needed based on the risk assessment.
- Implement – Apply security controls within the environment and systems using verifiable system security engineering practices and security configuration settings.
- Assess – Determine security control effectiveness related to proper implementation, operation intent, and security requirements for the system and environment.
- Authorize – The Authorizing Official should examine the results of the security controls assessment to verify if the risk level is acceptable.
- Monitor – Regularly monitor the controls in place and track signs of change, attack attempts, etc. that may affect controls. Control effectiveness should be reassessed as needed.
How to Prepare for a NIST Risk Assessment
The objectives and advantages of thorough preparation include establishing effective communication between top management of business process levels, system owners, and executives within the organization. It helps identify common controls and baselines for the entire organization, while prioritizing resources for high-value assets and high-impact systems that merit extra protection.
Formulate a Plan
Before embarking on a NIST risk assessment, it’s important to have a plan. This should be based on specific goals and constraints and include where and how information will be gathered, as well as the analytic approach that will be utilized.
Assign Roles
During a risk assessment, it will be crucial to know who is responsible for the various tasks involved. The key roles are categorized according to either organization level or system level. Here is a brief overview of these key roles.
Organization Level
-
- Head of Agency – Facilitate an organization-wide discourse for considering all sources of risk and oversee the risk management process.
- Chief Information Officer – Ensure that an effective security program is in place, set expectations and requirements, secure adequate funding and resources to support the security program.
- Mission/Business Owner – Develop an organization-wide control baseline.
- Risk Executive – Continually assess security and privacy risk. Develop and implement a strategy for continual monitoring of control effectiveness.
- Senior Agency Information Security Officer – Identify, document, and disclose common controls. Assign roles related to security risk management, making sure there are no conflicts of interest.
- Senior Agency Official for Privacy – Continually assess privacy risk. Assign roles related to privacy risk management, making sure there are no conflicts of interest. Develop and implement a strategy for updating privacy reporting requirements.
- Senior Accountable Official for Risk Management – Align information security management processes with strategic, operational, and budgetary processes.
Continually assess security and privacy risk. Implement a comprehensive, continuous monitoring program to maintain the initial system or common control authorizations, and security and privacy reporting requirements.
System Level
- Enterprise Architect – Implement an enterprise architecture strategy including effective security and privacy solutions. Collaborate with system owners and authorizing officials to facilitate authorization boundary determinations.
- Information Owner – Identify the types of information that will be processed, stored, and transmitted by the system.
- Mission/Business Owner – Define mission/business functions and processes that the system must support.
- System Owner – Identify stakeholders who have an interest in the system, assets that require security and privacy protection, authorization boundary, protection needs and security and privacy requirements. Conduct a system-level risk assessment and regularly update the risk assessment.
- Senior Agency Official for Privacy – Identify phases of the information life cycle. Collaborate with system and security officials to ensure compliance with privacy activities.
- System Security or Privacy Officer – Perform system-level security and privacy risk assessments.
Define the Scope
The scope is essentially the outline of the risk assessment. Your team must determine which areas of the organization, time frame, and system components will be included in the assessment.
Set a Timeline
Your team should build a realistic timeline that works back from any hard deadline and leaves plenty of time for gathering evidence, mitigation, and improvements. Then, looking forward, set a schedule for regular risk assessments and updating the overall risk management process.
Outline Communications
Because one of the goals of performing a NIST risk assessment is to improve communication about vulnerabilities and mitigation efforts throughout the organization, it’s best to outline a schedule for reporting results. Define the information that needs to be shared with executives, top management, and system owners and the frequency of these updates.
Create a Strategy for Systematic Improvement
When your organization is discussing the goals of the risk assessment, it’s also necessary to decide how the results will be utilized. Apart from the need to modify controls in order to better address risk, your team should define how results will inform company decisions and impact budgeting processes.
Let Us Build a NIST Risk Assessment Checklist for Your Organization
Risk assessment preparation is a highly customized process. The objective is to assess current security measures and make a clear roadmap for mitigation and future improvement. I.S. Partners can guide you through this process. Rely on us for practical advice and individual attention; request a free quote to get started.

