This year, in particular, there has been a relentless, unmistakable uptick in cyberattacks on entities in the healthcare industry. Ransomware and other malicious attacks have targeted medical and science facilities in hopes of taking advantage of the global emergency and accessing data that is more valuable than ever.
In 2019, 41.4 million patient records were breached and that number is expected to be similar in 2020, according to Health IT Security.
Today’s healthcare professionals need to know how to protect their institutions, as well as patient privacy. So, we have put together some clear answers for your most pressing questions about preventing data breaches and ensuring data security.
What is a Healthcare Data Breach?
Any unauthorized access of protected health information (PHI) is considered a healthcare data breach. Malicious attackers target the IT network and infrastructure of medical, pharmaceutical, and biotech facilities in order to exploit and monetize sensitive data.
Some hackers are looking to steal intellectual property from the facility itself, while breached personal records can be used for activities like identity theft. Stollen patient data – names, addresses, financial information, and social security numbers – are often sold on the dark web and used to take out fraudulent lines of credit.
What is the Probability of a Data Breach for a Healthcare Organization?
Unfortunately, data breaches are not uncommon in the health care sector. In the last decade, there have been 2,100 single healthcare data breaches in the United States. “In 2019, healthcare data breaches were reported at a rate of 1.4 per day,” according to HIPAA Journal.
This means that the probability that a malicious attack will be attempted are high for any one organization. Yet, the probability that an attack will be successful depends on the security policies and procedures that an organization has in place. In fact, we don’t know how many attempted attacks there are in healthcare over a given period of time; we only have statistics about actual breaches reported.
The good news is that, with the help of risk management programs, businesses are getting better and better at detecting hacking attempts, preventing breaches, and minimizing damages.
What are the Repercussions of Data Breaches in Healthcare?
The HHS Office of Civil Rights (OCR) is responsible for enforcing HIPAA Privacy and Security Rules for most covered entities. The OCR enforcement process includes investigating complaints about potential HIPAA violations and carrying out compliance reviews for covered healthcare entities.
Penalties for HIPAA non-compliance are expensive. They vary from $100 to $50,000 per violation – or per record breached – with a maximum fee of $1.5 million per year for identical violations. Fines increase depending on the number of patients affected and the degree of neglect which led to the breach. Penalties for HIPAA violations can also include jail time.
But fines imposed by the OCR are not the only repercussions for data breaches in the medical field. The average data breach costs healthcare entities $6.5 million, which is higher than any other industry. And these costs are on the rise, with the negative impact lasting for several years following the incident. For example, healthcare breaches tend to cause a large loss of business because of the importance of trust among patients. Identifying, containing, and resolving the technical issue that enabled hacker access to sensitive data also requires a robust effort, an average of 245 working days.
To date, the largest data breach in this industry – affecting Anthem, Inc. in 2015 – cost the insurance giant $16 million in fines imposed by the OCR. But it also cost the company $115 million in a class action settlement for the cybersecurity failure that exposed the personal information of 79 million patients. Plus, it agreed to pay out $39 million settlement to a group of State Attorney Generals involved in investigating the hack. These are just some of the costs that can add up quickly.
“Cybercrime represents big money for cybercriminals, and unfortunately that equates to significant losses for businesses,” Wendi Whitmore, Global Lead for IBM X-Force Incident Response and Intelligence Services. By 2021, some experts expect the damages caused by cybercrime to reach $6 trillion for healthcare companies.
How do Security Controls Prevent Healthcare Data Breaches?
Security controls are the actual measures put in place by a covered entity as part of a threat detection and risk management program. When implemented correctly, security controls work to avoid, detect, counteract, or minimize security risks to their computer systems and sensitive patient information.
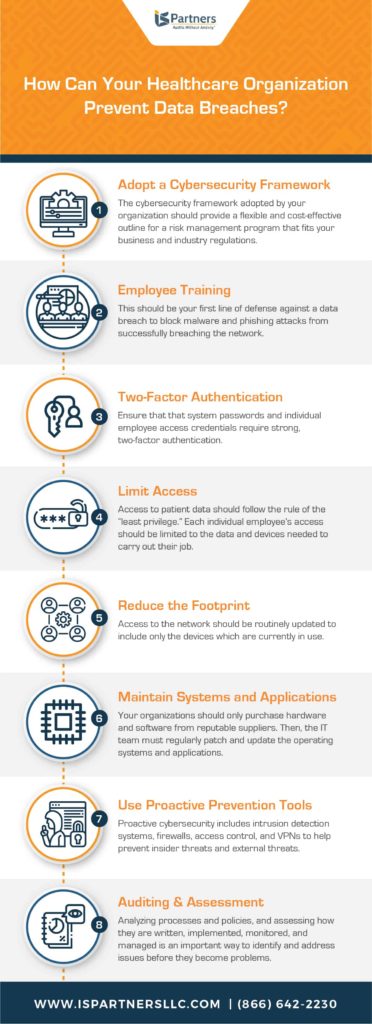
How Can Data Breaches be Prevented in the Healthcare Industry?
Preventing data breaches, in any industry, requires a complex combination of micro tasks. These range from updating policies for employees to installing network patches. General recommendations include conducting a HIPAA and HITECH audit to identify gaps in the current security controls, keeping network security measures up to date, and providing continual cybersecurity training for employees.
But effective cybersecurity prevention requires a risk management program that is organized on the macro level. A cybersecurity framework is a powerful tool for building and running a successful risk management program. It is a system of standards, guidelines, and best practices to manage risks effectively.
Why Choose the HITRUST CSF Framework for Cybersecurity Risk Management?
The HITRUST CSF is a revolutionary security and privacy framework for protecting vital electronic healthcare information. Healthcare, technology, and information security leaders worked together with HITRUST to build the HITRUST CSF framework. It was developed to address the many security, privacy and regulatory challenges that face healthcare organizations, and organizations in other industries that handle sensitive data.
The HITRUST CSF helps organizations in the healthcare industry to prevent data breaches through guidance on implementing the right policies and procedures, relevant to the size and activities of the organization, and how to improve them over time. The HITRUST CSF acts as an actionable guide that addresses specific threats facing electronic data in the healthcare industry.
It’s a unified security and privacy framework that serves as a baseline and combines multiple regulations and standards, including HIPAA, HITECH, NIST, ISO, PCI, and COBIT. The comprehensive framework simplifies compliance efforts with these numerous regulatory requirements, while supporting a strong risk management program to protect patient privacy and consumer confidentiality. The framework is flexible, enabling security controls to be adapted and keep the organization’s IT system up to date within the continually and rapidly changing digital landscape. It also defines alternate controls when necessary, and works for both HIPAA-bound covered entities and their business associates.
Some of the basic security risks that the HITRUST CSF helps organizations to combat include the following:
- Security control redundancies and inconsistencies at all levels.
- Misinterpretation of cybersecurity standards and regulations.
- A lack of communication within the IT department and with third-party service providers about shared responsibilities.
- Confusion regarding acceptable minimal controls and application of those controls.
- Potential and future risks, as well as evolving cyberthreats.
Get more information on the HITRUST Certification Process and refer to our Dictionary of HITRUST CSF Terminology.
Prevent Compromised Healthcare Data with HITRUST Assurance
Whether you want help figuring out where to start, need a professional to perform a HITRUST CSF Assessment, or are ready to begin the HITRUST CSF Certification process, I.S. Partners is here. Contact us online or call us at 215-675-1400 to learn more about how we can help you save time and effort while avoiding risk.