If your service organization’s controls directly—or will eventually—affect the internal controls regarding financial reporting, it is highly likely that you need to perform an SOC 1® audit. Any time that you offer specialized services, such as SaaS or a cloud suite of offerings, and you have access to any customer information, an SOC report is an organic part of such an engagement.
The purpose of this reporting framework is to allow you to demonstrate that your organization has proper internal controls and processes in place to address matters of information security and underlying compliance risks.
How to Prepare for an SOC 1 Audit
So, basically, if you are reading this post, you probably have some SOC assessment preparation on deck. You may feel some stress, whether it is your first time going through the process, or if you are concerned about some looming issue. No need to worry or get bogged down with stress because we have come up with our top nine steps to help you prepare for a smooth SOC examination.
Define the Objectives
Ask yourself what your user entity wants to learn from the audit and resulting SOC 1 report. If they want to learn something specific about your organization’s financial controls, then a SOC 1 audit is likely the right choice.
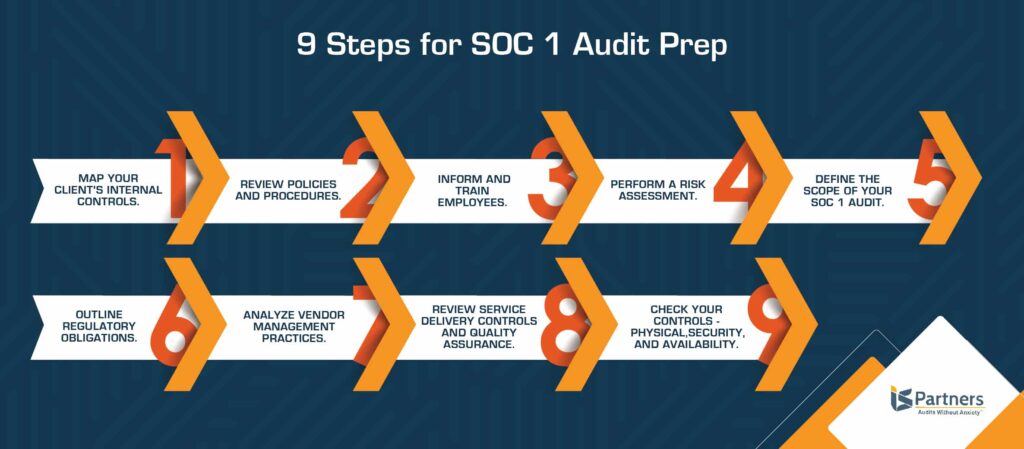
Map the Internal Controls.
It sounds simple enough, but this step is important. Before you start gathering information and formally preparing for your SOC 1 audit, review documentation of the internal controls. Also, make sure to ask questions about anything that will help your audit run more smoothly. Key information includes the type of business, the industry or market of operation, the operating environment used, and the general service offerings. This information will help you align your internal controls to theirs more easily.
Review Policies and Procedures.
Your written policies and procedures have it all laid out for you to use as a guidepost. Taking a step back to when you developed your policies and procedures, make sure that they are written down, typed in and saved for your regular updates and review. However, you most likely did all of that, so go ahead and pull up your formally written and fully documented collection of policies and procedures. They are paramount because they serve as the baseline against which you will compare the results of your SOC audit.
Written policies and procedures also help employees stay on course since they can refer to your organization’s expectations for compliance, as well as possible consequences for non-compliance.
Related article: How to Write a Solid Written Assertion for Your SOC 1 Audit.
Inform and Train Employees.
This step goes directly along with your written policies and procedures, which mean little if your employees and managers are not on board and following them. Make sure you have documented all training sessions for all employees, providing answers to the following types of questions:
- Did all staff attend?
- Did staff understand the materials?
- Did staff have specific questions on key concerns?
- Did all staff sign an attendance form, as well as a form indicating understanding of the materials?
- Have staff members made errors relating to training, indicating that there was some possible lapse in communication that you might need to clarify?
The answers to these questions can help you understand why certain errors might have been made, as well as where your team is excelling.
Perform a Risk Assessment or Readiness Assessment.
Once you’ve determined the above, it’s time to do an internal assessment to help identify and close the gaps.
Most compliance and information security frameworks, audits, standards and regulations require some type of risk assessment. A formal risk assessment, performed with the assistance of a trusted auditing firm, is the best way to officially kick off your SOC audit preparation. Once you have performed your risk assessment, you can easily identify any risks in your control environment, which allows you to implement internal controls more reasonably and with optimal control.
A readiness assessment can help you determine your preparedness for a SOC audit. You can either choose to perform a readiness assessment on your own, or you may engage an auditing firm to perform your review. Such an assessment gives you a chance to perform a warm-up for the official audit, which can help you sort out any issues in advance.
Define the Scope of Your SOC Audit.
Defining the scope of your SOC 1 audit helps you figure out your overall goals. It’s imperative to define the scope of the audit early on in the process; not doing so could lead to excessive delays and potential cost overrun. Essentially, what do you want to learn from this audit? Decide whether you will focus on physical locations, a relevant testing period, and which specific personnel need to participate in the audit.
The scope of your SOC 1 audit may involve issues such as classes of transactions, procedures for processing and reporting transactions, accounting records of the systems and report preparation for users. Here are some questions that will help you determine the scope of your SOC 1 Audit:
- Are there any reporting assessments you’ve done in the past that can help you determine the proper scope?
- What control objectives are you using to form the basis of your reporting?
- Which subservice organizations do you work with and how do you intend to include them?
Outline Regulatory Obligations.
Certain industries are more heavily regulated than others, such as healthcare and payment cards. You may also be subject to certain regulations or standards, based on where your business is located or where your customers are located. You may be subject to compliance for one or more of the following regulations and standards:
- GLBA (Gramm-Leach-Blieley Act) applies to financial institutions that provide products or services such as loans, financial or investment advice, or insurance – to explain their information-sharing practices to customers and to safeguard sensitive data.
- HIPAA/HITECH for the healthcare industry
- PCI DSS for the payment card industry
- GDPR for businesses serving customers living in one of the member states within the European Union
- CCPA for businesses working with customers residing in California
- NERC CIP standards associated with the Bulk Power System across North America
There are many additional standards and regulations, so make sure to review your contract and talk to your SOC auditor to make sure you have everything covered.
Analyze Vendor Management Practices.
Working with your trusted vendors is essential to your business operations, but you need to ensure that their practices align with those of your company. While you understand and have adapted to the risks involved, it is important that you take a closer look at how acceptable those risks are, in accordance with your contract. Any business that you work with that may have some degree of access to your networking system should vet their employees by performing background checks. You may also ask for a signed non-disclosure statement and periodically review their compliance status regarding regulatory requirements and information security.
Review Service Delivery Controls and Quality Assurance.
It is important that you do not overlook any operational risks that might affect your service delivery controls. Make sure to map out your plans to always ensure service delivery through the creation of a data flow diagram that depicts the life cycle of your service delivery model.
Check Your Controls.
We thought we might compile the “controls” matters into one section. In conjunction with your CPA firm, define the controls to be tested and make sure that they have been reviewed by process owners and any of the stakeholders at the CPA firm who may be reviewing and/or signing off on the report to ensure everyone is in agreement. Let’s take a closer look at each relevant control to see how you can best prepare:
- Physical Controls – These controls cover restricting access to your business’s physical environment. You might draw on your records regarding how people enter and exit your facility and how carefully you track visitors while they are on the premises. It is particularly important to limit access to any areas where your files and stored data are accessible.
- Security Controls – Security controls involve CIA, which stands for Confidentiality, Integrity and Availability. You must document any occurrence that any information has been compromised, whether through theft or some type of physical damage.
- Availability Controls – These types of controls involve things like Business Continuity and Disaster Recovery Plans in case of some type of natural or human-induced disaster or situation that may limit access to your data. Additional availability controls to keep on your radar include network monitoring and data backups.
Hire a CPA at a Trusted Auditing Firm
Your CPA can help guide you through the process of performing any of the SOC 1 audits. He or she can also help you work through the various tips listed here, as well as many other tips that can help ease the process for you.
When it is time for your official audit, your auditor will do the following:
- Work with you to agree upon testing dates.
- Provide a list of requested evidence (usually a month in advance of the audit).
- Visit your site for interviews, walkthroughs and document reviews.
- Document testing results and work with you to clarify any testing exceptions.
- Prepare and Deliver a SOC 1 report to you.
Related article: What’s the Difference Between SOC 1 vs. SOC 2 Reports?
Do You Need Some Help Preparing for a SOC 1 Audit?
It is no secret that SOC audits seem extremely complex when first getting started. Also, there are simply some steps that—for some reason—consistently trip up different service organizations. Add in the fact that you and your team are trying to juggle daily responsibilities with this important multi-step auditing process, and it makes sense that you might have questions or could use some reinforcements during preparation.
Our auditors at I.S. Partners, LLC. have years of experience in helping service organizations remain in good standing with user entities. Our team members understand how stressful SOC audits can be for seasoned service organizations. They also understand how overwhelming these audits may seem to those new to the service organization industry and auditing procedures. Let us pitch in to help you streamline the process with the above-mentioned steps and much more, specific to your service organization. We’ll help you develop a consistent plan that builds confidence with each SOC 1 assessment.
Contact us with any SOC 1 Type I or SOC 1 Type II questions you may have to protect your stakeholder relationships, reputation among your customers, and the value of your brand.
SOC 1®, SOC 2® and SOC 3® are registered trademarks of the AICPA (American Institute of Certified Public Accountants). The AICPA® Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy is copyrighted by the Association of International Certified Professional Accountants. All rights reserved.