Key Takeaways
1. SOC 2 audits are crucial for tech-service organizations storing client data in the cloud.
2. A SOC 2 audit is an examination conducted under the Trust Service Criteria, ensuring data protection and privacy.
3. I.S. Partners is a SOC 2 audit firm and CPA (Certified Public Accountant) that offers comprehensive SOC services, including SOC 2 Type I and Type II.
What Is SOC 2?
SOC 2 is a cybersecurity compliance framework created by the American Institute of Certified Public Accountants (AICPA) that ensures third-party service providers store and process client data securely.
SOC 2 focuses on the security measures established by an organization to ensure proper data handling and protect them from malicious intrusions. This security framework generally applies to organizations handling sensitive customer data, such as Software as a Service (SaaS) providers, data centers, and healthcare institutions.
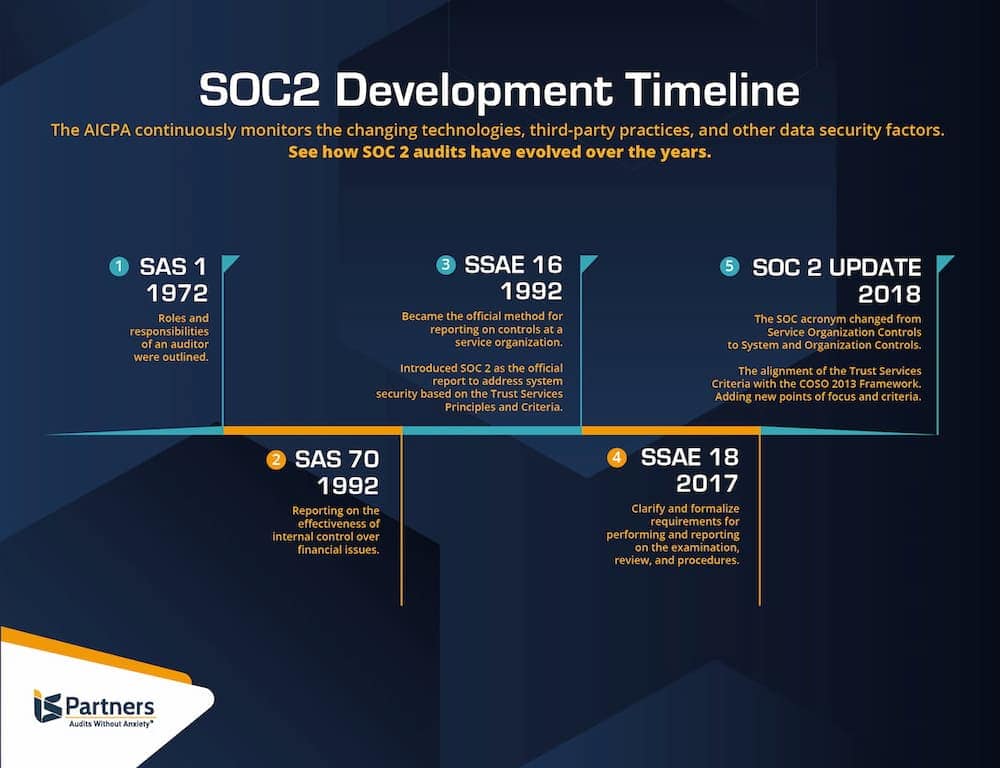
What is a SOC 2 Audit?
A SOC 2 audit is an assessment of a service provider or organization’s controls and information systems that relate to security, availability, processing integrity, confidentiality, and privacy. The audit is based on the American Institute of Certified Public Accountants (AICPA) Trust Services Criteria (TSC) of the Auditing Standards Board and is carried out by an independent certified public accountant. It ensures service providers securely manage data to protect an organization’s privacy and interests.
A SOC 2 audit, although voluntary, is a critical process that every data-handling business should undergo to help protect their sensitive business and customer data from attacks that include data theft, ransomware, and malware installation. Mishandled data can cost enterprises a pretty penny, and this is what a SOC 2 audit and compliance aim to prevent.
Audits are performed by Certified Public Accountants (CPAs) or audit firms (like I.S. Partners!) that have been commissioned by the AICPA. Not all accountants are CPAs, so you cannot hire a regular accountant to conduct a SOC 2 audit.
What Are SOC 2 Audit Types?
The two main SOC 2 audit types are Type 1 and Type 2 and are based on the required comprehensiveness of the evaluation
A Type 1 report verifies that an organization’s systems and processes are compliant at a specific time, whereas a Type 2 report verifies that the organization’s compliance has been maintained over a period of time.
The time period for a Type 2 report is usually 12 months but can be as short as three months. Both types of SOC 2 audits follow the same principles. Their main difference lies in the particular timeframe being evaluated.
The chart below shows the differences between a SOC 2 Type I audit and a SOC 2 Type II audit.
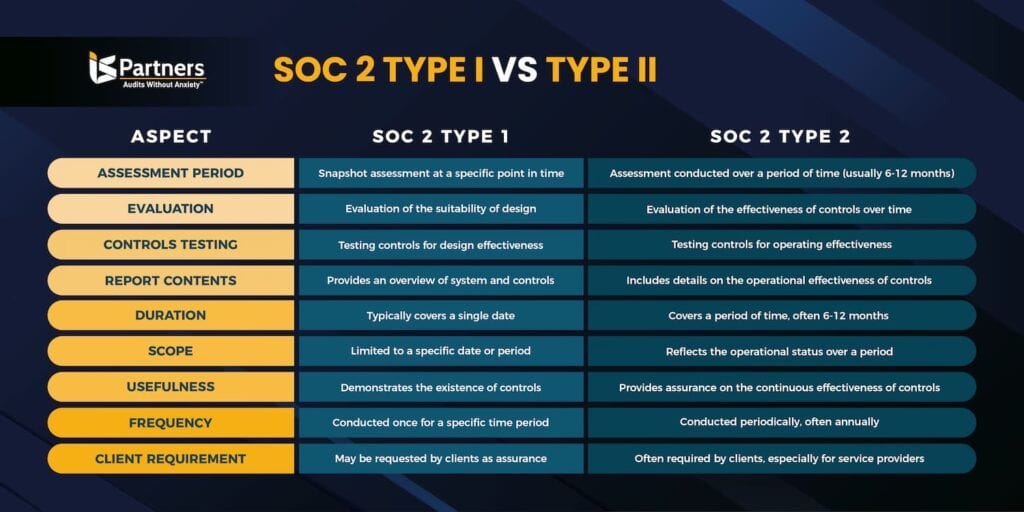
- SOC 2 Type I – This type of audit examines the controls that service organizations use to address any or all five of the Trust Services Criteria. It evaluates the service organization’s systems to determine if they are effectively designed to meet relevant trust criteria at a specific point in time. Type I audits effectively describe whether the system needs improvement and are often used for preliminary evaluations.
- SOC 2 Type II – This audit type includes additional attestation that a service organization’s controls undergo testing for operating effectiveness over a period of time. The audit system evaluates the described security framework more in-depth by adding the factor of continuous usage over time. Type II audits typically take 6 to 12 months to conclude.
Choosing between the two types of SOC 2 audits will vary depending on your resources, including time, funds, and overall goals. Some organizations use the Type I audit as their main goal is to check whether they have the right security structure or not. These organizations then transition into using the Type II audit to see if their security controls are effective over time. This strategy is effective if a smaller business is trying to gain footing in the industry.
In some cases, organizations opt for a Type II audit straight away. Doing so can save time and cost in a larger perspective and can offer a more comprehensive insight.
Consult with I.S. Partners’ expert Certified Public Accountants (CPA) to understand which type of audit fits your needs best. Save time from contemplating and let our team do the heavy lifting for you. Contact us now and get a quote.
Why Are SOC 2 Audits Important?
Service organizations have become increasingly invaluable to growing organizations for various vital services. Also referred to as the AICPA Guide Reporting on Controls at a Service Organization Relevant to Security, Availability, Processing Integrity, Confidentiality, or Privacy, the SOC 2 audit is used by companies that outsource services with access to customer data.
Here are more reasons why SOC 2 audits are important:
- Data security and privacy assurance. SOC 2 guidelines were developed to ensure that customer data remains confidential, secure, private, and available for use when needed. Additionally, they provide assurance regarding complete, accurate, timely, and authorized system processing. The SOC 2 audit report is an attestation report verified by a trusted registered public accounting firm, which a service organization can provide as proof of compliance to its user organizations.
- Effective risk management strategy. The audit includes the identification of any vulnerable points of your security system. Through this, you can fortify your security strategies and further strengthen your system against data breaches.
- Customer confidence. Trust and consumer confidence are critical for services that handle data. Being audited by professionals and passing compliance tests assures your customers that their data is handled correctly. This aspect serves as a competitive advantage in any industry.
- Compliance with regulations. Undergoing a SOC 2 audit can help your organization comply with data handling and privacy regulations. These regulations can include HIPAA, ISO, and GDPR.
- Continuous improvement. In addition to verifying vulnerabilities in your security system, a SOC 2 audit can help identify points for improvement and suggest the best solutions. Organizations can enhance their operations, increase efficiency, and better protect customer data by addressing these areas.
In addition to being a requirement by many organizations, undergoing a SOC 2 audit displays your business’s commitment to protecting customer data. SOC 2 audits address security management issues while improving operational efficiency.
What Is SOC 2 Compliance?
SOC 2 compliance refers to an organization’s adherence to the security framework’s fundamental criteria as established by the AICPA. Compliance involves establishing the required security controls and undergoing a SOC 2 audit for verification.
Compliance with the SOC 2 requirements ensures an organization can securely handle data and protect information from breaches and other threats. It also implies that an organization has taken steps to address vulnerabilities identified from the risk assessment.
SOC 2 compliance is a continuous process and requires regular maintenance, verification, and improvement. This ensures that an organization’s security system can adapt to the evolving traits of cybersecurity threats.
What Are SOC 2 Compliance Requirements?
As mentioned, the main SOC 2 compliance requirement is having a comprehensive security system and strategy for handling and protecting data. Achieving this main goal consists of several layers of steps and criteria.
The main requirements of SOC 2 compliance are based on five core criteria – security, availability, processing integrity, confidentiality, and privacy – which are further discussed in the next section.
Organizations can choose which aspect to focus on during a SOC 2 audit. Among the five criteria, security is mandatory; nine key, common criteria must be fulfilled under this criteria.
Here is a list of the nine common criteria for security, otherwise known as the CC-series:
- CC1 – Control environment
- This criterion describes your organization’s culture of operations and accountability. It requires your team to have a clear job structure and segregation of responsibilities for the efficiency of operations.
- CC2 – Communication and information.
- Under this criterion, your team must establish clear internal and external communication lines. It requires your organization to have a seamless information transfer mode between management, employees, customers, and third-party members. Policies on how information is handled and flows through the organization are necessary.
- CC3 – Risk assessment
- An organization handling information must have an established risk assessment strategy to identify any potential threats to data properly. This means performing analysis and setting up controls based on findings.
- CC4 – Monitoring controls
- Data handling businesses must have regular systems in place that will allow them to measure their operational efficiency and immediately detect non-compliance. A comprehensive monitoring system can help teams address problems and accurately communicate the threat to all concerned teams.
- CC5 – Control activities
- This criterion identifies the need to establish the appropriate controls in case threats breach your security system. Proper internal control activities must be incorporated in all stages of the operation to ensure security,
- CC7 – System operations
- System operations criterion describes the need for organizations to establish effective corrective action plans and appropriate recovery strategies in case of a data breach.
- CC8 – Change management
- Organizations must have a system for verifying any change that will occur in the security system, whether it is a corrective step or an improvement of the existing system. This will ensure the changes work as intended and will not cause problems.
- CC9 – Risk mitigation
- Risk mitigation must be reflected in all of the operations implemented by a business.
The mentioned nine criteria describe the overlapping requirements and security measures included in the five main Trust Service Criteria. They are the summary of all the main security requirements that every data-handling organization should have.
The audit will also require your organization to comply with a comprehensive SOC 2 controls list.
Remember that these common criteria are not exhaustive and that there are other SOC 2 requirements. Use these criteria as the backbone of your SOC 2 framework.
What Is the SOC 2 Framework: The Trust Service Criteria?
The SOC 2 framework is the system used to evaluate a service organization’s security system and is based on the five Trust Service Criteria – security, availability, confidentiality, privacy, and processing integrity.
The Trust Service Criteria framework guides the SOC 2 auditing and reporting process. In a SOC 2 audit process, you can ask the auditor to focus on one, if not all, criteria. The auditor can suggest which criteria to focus on based on your needs.
Below are the five Trust Services Criteria:
Security
The Security criterion is the foundation of a SOC 2 audit. All audits will include this criterion. A business’s data and computing systems are fully protected against unauthorized access, inappropriate information disclosure, and possible system damage.
The security criteria minimize risks that might compromise the processing integrity, availability, confidentiality, or privacy of data or systems that may affect the entity’s ability to meet its objectives.
Availability
All information and computing systems are ready and operational to meet the entity’s objectives. Availability of information requires proper service organization controls and must clearly state which entities are only allowed to access the information.
This criterion does not have any performance level indicators. Despite this, it is critical to get it correctly as it can influence your relationship with your customers.
Availability also refers to accessing the required information when needed, with the least downtime that will hinder the operation’s efficiency. Measures such as redundant systems, disaster recovery plans, and proactive monitoring are key to ensuring high availability.
Processing Integrity
All system processing is complete, accurate, valid, timely, and authorized to ensure the entity meets its objectives. Processing integrity focuses on your cloud environment.
This criterion focuses on ensuring that all security measures protect data integrity and that information is free from unauthorized access and errors. The criterion also includes requirements for swift detection of errors and systems for validating the information released to the customer.
Confidentiality
Any information designated as confidential remains secure to meet the entity’s objectives. The confidentiality criterion aims to identify the service organization’s capabilities to protect sensitive information from unauthorized disclosure.
Security measures that ensure confidentiality involve encryption, access controls, data masking, and comprehensive data agreements. The criterion also requires the business to set up contingency plans in case of a data breach when information must be destroyed.
Privacy
All personally identifiable information collected, used, retained, stored, disclosed, or disposed of must meet the entity’s objectives. Privacy criteria focus on protecting personal information as privacy laws and regulations require.
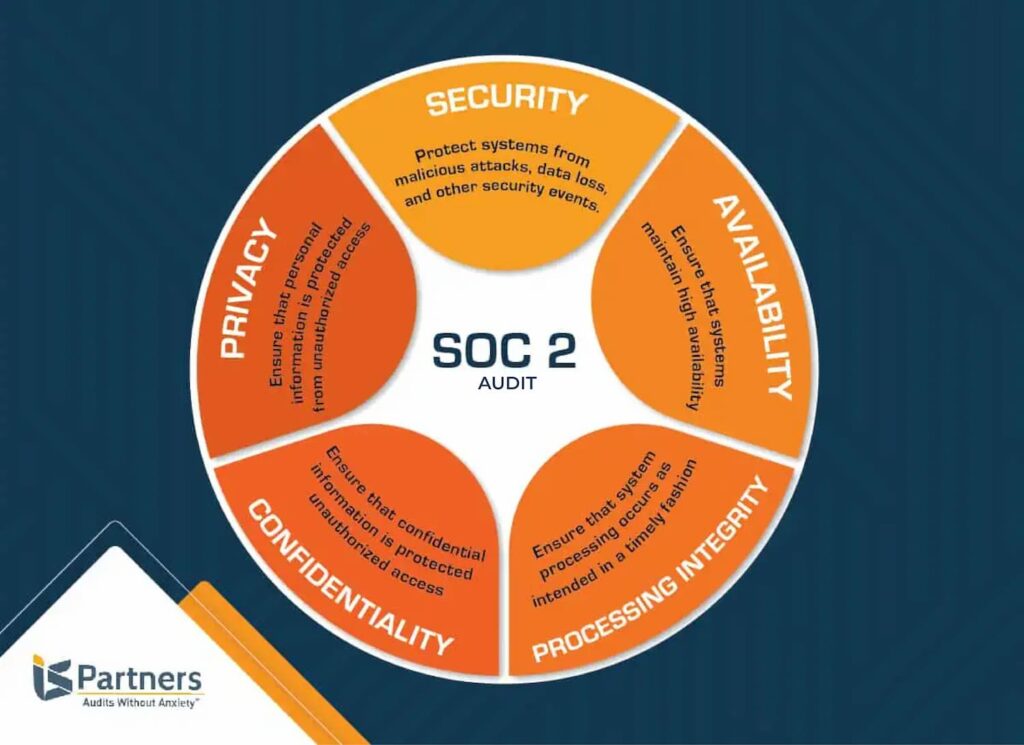
Each area provides the key information that helps determine if a service organization meets the Trust Service Criteria. However, each SOC 2 report will be unique to each individual organization.
Depending on what the organization requires and wants to focus on, the SOC 2 audit framework and report will vary. Consult an expert from I.S. Partners, and let us guide you through the criteria your business requires.
How to pass a SOC 2 Audit
The keys to passing a SOC 2 audit are careful preparation, a thorough understanding of the regulations, and following the best practices for information security.
It pays to understand the SOC 2 framework, but your chosen auditor will guide you through the process. What you need to do to streamline the process and ensure passing is to prepare all needed documents.
Here are some of the best practices to pass a SOC 2 audit:
- Understand the SOC 2 requirements and data privacy laws. One of the main reasons why you need to secure information is because the law requires you to do so. Your entire team must be familiar with what is needed from your business to avoid unnecessary business steps and make the entire audit process more accurate. This step includes familiarizing yourself with the SOC 2 criteria.
- Establish and properly record security policies. All businesses handling customer information must have adequate SOC 2 policies and standard operating procedures. Before the audit, your organization must have the basic security measures, such as system access, risk assessment, incident response plan, and defined security roles. All policies must be properly documented and equipped with a monitoring system as proof of compliance. This step includes regular evaluation of the policies for continuous improvement.
- Implement security controls. A SOC 2 audit will evaluate whether your security controls are properly applied. Security controls must be based on the identified vulnerabilities of your operations.
- Train employees. All employees involved in handling data must have proper training. This will help ensure your customers that professionals handle their data. Conduct regular employee training programs regarding the most advanced security controls and most recent threats.
- Choose a reputable auditor and engage consistently. Selecting the appropriate auditor will inevitably determine the success of your security controls. Every auditing firm has its specialty industry. Choose a firm or auditor who has worked in a similar industry. Once you have selected an auditor, ensure that your entire team or representatives consistently provide the needed information for efficient auditing.
- Address findings immediately. Your team must be prepared to address problems and findings during the audit process. The faster and more efficient your team addresses the findings, the more likely you will get the passing mark faster.
By following these steps and demonstrating a commitment to implementing effective internal controls and practices, your organization can increase its chances of passing a SOC 2 audit successfully and obtaining a favorable audit report.
Check out our detailed list of best practices to pass your SOC 2 audit here.
Check Your Compliance Status Now!
Do you want to know if your company satisfies the SOC 2 requirements? Use our free compliance checker quiz and allow us to help you determine which audit program your operations require.
Who Needs SOC 2 Audits?
SOC 2 audits were basically designed for service organizations handling sensitive customer information.
A SOC 2 audit plays an important role in regulatory oversight, as well as internal risk management processes and corporate governance. It provides client companies assurance about the security of data that is outside of their facilities and to which their service organizations have access.
Any organization that needs detailed information and assurance about the controls at a service organization may request a SOC 2 audit. The primary types of companies that undergo a SOC 2 audit include those that provide services like data hosting, colocation, data processing, cloud storage, and Software-as-a-Service (SaaS).
Specifically, organizations that may seek SOC 2 audits include:
- Cloud services
- SaaS
- Data centers
- Payment processors
- FinTech companies (e.g., banking and insurance)
- Healthcare organizations
- Human resources and payroll providers
These service providers must ensure that any data is transmitted, stored, processed, and disposed of according to the SOC guidelines set by the AICPA. SOC 2 audits may be performed as part of a regular information security program or if the user organization suspects a data security issue with one or more of the criteria at the service organization.
Is a SOC 2 Audit Mandatory?
No, SOC 2 audit is not mandatory for all organizations and is not part of any data privacy law or regulation. Despite this, customers and other stakeholders often require a SOC 2 audit.
Unlike HIPAA, PCI DSS, and GDPR laws, service organizations undergo a SOC 2 audit voluntarily.
SOC 2 Report vs SOC 2 Attestation – What Is the Difference?
A SOC 2 Report and SOC 2 Attestation both reflect the results of a SOC 2 audit. Their main differences lie in the comprehensiveness and goal of being written.
In general, a SOC 2 final report is a detailed summary of the audit, including any required improvements, vulnerabilities, and identified risks. On the other hand, an attestation, otherwise known as a clean report, validates that a service organization’s security system is credible and adequate enough to protect customer information.

What Is Included in the SOC 2 Audit Report?
In a SOC 2 audit, there is no need to focus on financial reporting controls since those are covered in a SOC 1 audit. The SOC 2 report evaluates a business’s non-financial reporting controls relating to the security, availability, processing integrity, confidentiality, and privacy of a system.
In the SOC 2 audit report, the auditor will provide a written evaluation of the service organization’s internal controls. It will contain a determination by the accounting firm as to whether the appropriate controls are in place to address each of the selected TSCs.
There is no guarantee that the CPA’s opinion will be positive. A crucial stage in preparing for a SOC 2 Audit is conducting a SOC 2 Readiness Assessment.
A SOC 2 report’s validity is only up to 12 months. A new audit must be scheduled to continue compliance. If a schedule lapse occurs, a service organization can issue a SOC 2 Bridge Letter in place of the report, until an official audit is made.
What Is Included in the SOC 2 Attestation Report?
Unlike a SOC 2 report, a SOC 2 attestation contains only the verification that a service organization has complete and credible security controls. In simple terms, an attestation is the formal declaration that your organization has passed the SOC 2 audit.
It verifies the information from a SOC 2 report and whether it is fairly written based on the chosen criteria. A CPA or an accounting firm similarly provides an attestation.
Get the Best Professional Assistance for SOC 2 Audits from I.S. Partners, LLC
We cannot stress enough how important it is to choose the right auditing firm for your SOC 2 audit to succeed. With over 20 years of experience conducting SOC 2 compliance audits, I.S. Partners is the best solution for your SOC 2 audit needs.
The I.S. Partners, LLC SOC 2 team regularly works with user and service organizations to help both parties achieve top-level compliance for a healthy and secure business relationship that benefits everyone involved. Contact our office to get things rolling and benefit from our SOC 2 services.
FAQs
SOC 1®, SOC 2® and SOC 3® are registered trademarks of the AICPA (American Institute of Certified Public Accountants). The AICPA® Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy is copyrighted by the Association of International Certified Professional Accountants. All rights reserved.




